 |
HP OpenVMS System Services Reference Manual
$SET_RETURN_VALUE (Alpha and I64)
On Alpha and I64 systems, sets the return values or condition codes in
the Mechanism Array, independent of the architecture.
Format
SYS$SET_RETURN_VALUE mechanism_arg, return_type, return_value
C Prototype
int sys$set_return_value (void *mechanism_arg, unsigned int
*return_type, void *return_value);
Arguments
mechanism_arg
| OpenVMS usage: |
mechanism vector address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
The address of the location of the mechanism vector. If the
mechanism_arg argument is 0, the mechanism vector for
the currently active signal is used.
If the address of the return_type argument is 0, the
return_value argument is fetched by value and is
treated as return-type PSIG$K_FR_U32. This combination of arguments can
be used to set a condition code, such as SS$_ACCVIO, as a return value.
return_type
| OpenVMS usage: |
integer |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by reference |
The address of the location of a longword that contains one of the
function return signature codes.
If the address of the return_type argument is 0, the
return_value argument is fetched by value and is
treated as return-type PSIG$K_FR_U32. This combination of arguments can
be used to set a condition code, such as SS$_ACCVIO, as a return value.
return_value
| OpenVMS usage: |
buffer |
| type: |
scalar |
| access: |
read only |
| mechanism: |
by reference |
The address of the location that contains a value of the appropriate
type. The referenced value is read as a longword, quadword, or
octaword, depending on the return_type.
If the address of the return_type argument is 0, the
return_value argument is fetched by value and is
treated as return-type PSIG$K_FR_U32. This combination of arguments can
be used to set a condition code, such as SS$_ACCVIO, as a return value.
Description
The Set Return Value service allows the caller to specify return values
and condition codes in the Mechanism Array, independent of the
architecture.
Required Access or Privileges
None
Required Quota
None
Related Services
None
Condition Values Returned
|
status
|
Success or failure. The given return value is placed in the appropriate
fields of the specified mechanism vector, according to the return type.
|
|
SS$_NORMAL
|
The service completed successfully.
|
|
SS$_BADPARAM
|
|
|
SS$_NOSIGNAL
|
No signal is currently active for an exception condition.
|
$SET_SECURITY
Modifies the security characteristics of a protected object.
Format
SYS$SET_SECURITY [clsnam] ,[objnam] ,[objhan] ,[flags] ,[itmlst]
,[contxt] ,[acmode]
C Prototype
int sys$set_security (void *clsnam, void *objnam, unsigned int *objhan,
unsigned int flags, void *itmlst, unsigned int *contxt, unsigned int
*acmode);
Arguments
clsnam
| OpenVMS usage: |
char_string |
| type: |
character-coded text string |
| access: |
read only |
| mechanism: |
by descriptor |
Name of the object class. The clsnam argument is the
address of a descriptor pointing to a string that contains the name of
the object class.
The following is a list of the protected object class names:
CAPABILITY
COMMON_EVENT_CLUSTER
DEVICE
FILE
GLXGRP_GLOBAL_SECTION
GLXSYS_GLOBAL_SECTION
GROUP_GLOBAL_SECTION
ICC_ASSOCIATION
LOGICAL_NAME_TABLE
QUEUE
RESOURCE_DOMAIN
SECURITY_CLASS
SYSTEM_GLOBAL_SECTION
VOLUME
objnam
| OpenVMS usage: |
char_string |
| type: |
character-coded text string |
| access: |
read only |
| mechanism: |
by descriptor |
Name of the protected object whose associated security profile is going
to be retrieved. The objnam argument is the address of
a descriptor pointing to a string containing the name of the protected
object.
The format of an object name is class specific. The following table
lists object names and describes their formats:
| Object Class |
Object Name Format |
|
CAPABILITY
|
A character string. Currently, the only capability object is VECTOR.
|
|
COMMON_EVENT_CLUSTER
|
Name of the event flag cluster, as defined in the Associate Common
Event Flag Cluster ($ASCEFC) system service.
|
|
DEVICE
|
Standard device specification, described in the OpenVMS User's Manual.
|
|
FILE
|
Standard file specification, described in the OpenVMS User's Manual.
|
|
GROUP_GLOBAL_SECTION
|
Section name, as defined in the Create and Map Section ($CRMPSC) system
service.
|
|
ICC_ASSOCIATION
|
ICC security object name
node::association_name. The special node name, ICC$::, refers
to entries in the clusterwide registry. For registry entries, the
Access Access Type does not apply.
|
|
LOGICAL_NAME_TABLE
|
Table name, as defined in the Create Logical Name Table ($CRELNT)
system service.
|
|
QUEUE
|
Standard queue name, as described in the Send to Job Controller
($SNDJBC) system service.
|
|
RESOURCE_DOMAIN
|
An identifier or octal string enclosed in brackets.
|
|
SECURITY_CLASS
|
Any class name shown in the Object Class column of this table, or a
class name followed by a period (.) and the template name. Use the DCL
command SHOW SECURITY to display possible template names.
|
|
SYSTEM_GLOBAL_SECTION
|
Section name, as defined in the Create and Map Section ($CRMPSC) system
service.
|
|
VOLUME
|
Volume name or name of the device on which the volume is mounted.
|
objhan
| OpenVMS usage: |
object_handle |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by reference |
Data structure identifying the object to address. The
objhan argument is an address of a longword containing
the object handle. You can use the objhan argument as
an alternative to the objnam argument; for example, a
channel number clearly specifies the file open on the channel and can
serve as an object handle.
The following table shows the format of the object classes:
| Object Class |
Object Handle Format |
|
COMMON_EVENT_CLUSTER
|
Event flag number
|
|
DEVICE
|
Channel number
|
|
FILE
|
Channel number
|
|
RESOURCE_DOMAIN
|
Resource domain identifier
|
|
VOLUME
|
Channel number
|
flags
| OpenVMS usage: |
flags |
| type: |
mask_longword |
| access: |
read only |
| mechanism: |
by value |
Mask specifying processing options. The flags argument
is a longword bit vector wherein a bit, when set, specifies the
corresponding option. The flags argument requires the
contxt argument.
The following table describes each flag:
| Symbolic Name |
Description |
|
OSS$M_LOCAL
|
Do not update the master profile for the specified object. This flag
allows you to call $SET_SECURITY several times to modify a local copy
of a profile; once the modifications are satisfactory, you can clear
the OSS$M_LOCAL flag, set the OSS$M_RELCTX flag, and have $SET_SECURITY
update the master profile. The flag applies only to calls made with the
contxt argument.
|
|
OSS$M_RELCTX
|
Release the context structure at the completion of this request.
|
The $OSSDEF macro defines symbolic names for the flag bits. You
construct the flags argument by specifying the
symbolic names of each desired option.
itmlst
| OpenVMS usage: |
item_list_3 |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by reference |
Item list specifying which information about the process or processes
is to be modified. The itmlst argument is the address
of a list of item descriptors, each of which describes an item of
information. The list of item descriptors is terminated by a longword
of 0.
With the item list, the user modifies the protected object's
characteristics. The user defines which security characteristics to
modify. If this argument is not present, only the
flags argument is processed. Without the
itmlst argument, you can only manipulate the
security profile locks or release contxt resources.
The following data structure depicts the format of a single item
descriptor:
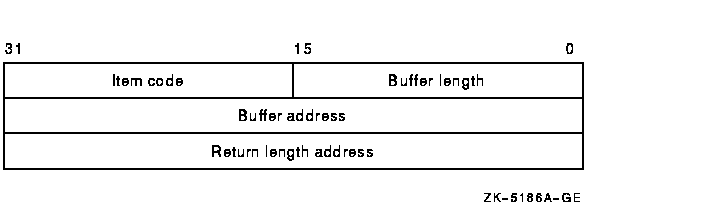
The following table defines the item descriptor fields:
| Descriptor Field |
Definition |
|
Buffer length
|
A word containing an integer specifying the length (in bytes) of the
buffer from which $SET_SECURITY is to read the information. The length
of the buffer needed depends on the item code specified in the item
code field of the item descriptor. If the value of buffer length is too
small, $SET_SECURITY truncates the data.
|
|
Item code
|
A word containing a symbolic code specifying the item of information
that $SET_SECURITY is to modify. The $OSSDEF macro defines these codes.
A description of each item code is given in the Item Codes section.
|
|
Buffer address
|
A longword containing the address of the buffer from which
$SET_SECURITY is to read the information.
|
|
Return length address
|
Not used.
|
contxt
| OpenVMS usage: |
context |
| type: |
longword (unsigned) |
| access: |
modify |
| mechanism: |
by reference |
Value used to maintain protected object processing context when dealing
with a single protected object across multiple
$GET_SECURITY/$SET_SECURITY calls. Whenever the context value is
nonzero, the class name, object name, or object handle arguments are
disregarded. An input value of 0 indicates that a new context should be
established.
Because an active context block consumes process memory, be sure to
release the context block by setting the RELCTX flag when the profile
processing is complete. $SET_SECURITY sets the context argument to 0
once the context is released.
acmode
| OpenVMS usage: |
access_mode |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by reference |
Access mode to be used in the object protection check. The
acmode argument is the address of a longword
containing the access mode. The acmode argument
defaults to kernel mode; however, the system compares
acmode with the caller's access mode and uses the
least privileged mode. The access modes are defined in the system macro
$PSLDEF library.
HP recommends that this argument be omitted (passed as zero).
Item Codes The following table provides a summary of item codes that
are valid as an item descriptor in the itmlst
argument. The table lists the $SET_SECURITY item codes and gives a
corresponding description. Complete descriptions of each item code are
provided after the table.
| Item Code |
Description |
|
OSS$_ACL_ADD_ENTRY
|
Adds an access control entry (ACE)
|
|
OSS$_ACL_DELETE
|
Deletes all unprotected ACEs in an ACL
|
|
OSS$_ACL_DELETE_ALL
|
Deletes the ACL, including protected ACEs
|
|
OSS$_ACL_DELETE_ENTRY
|
Deletes an ACE
|
|
OSS$_ACL_FIND_ENTRY
|
Locates an ACE
|
|
OSS$_ACL_FIND_NEXT
|
Positions the next ACE
|
|
OSS$_ACL_FIND_TYPE
|
Locates an ACE of the specified type
|
|
OSS$_ACL_MODIFY_ENTRY
|
Replaces an ACE at the current position
|
|
OSS$_ACL_POSITION_BOTTOM
|
Sets a marker that points to the end of the ACL
|
|
OSS$_ACL_POSITION_TOP
|
Sets a marker that points to the beginning of the ACL
|
|
OSS$_OWNER
|
Sets the UIC or general identifier of the object's owner
|
|
OSS$_PROTECTION
|
Sets the protection code of the object
|
OSS$_ACL_ADD_ENTRY
Adds an access control entry (ACE) pointed to by the buffer address so
that it is in front of the current ACE in the access control list
(ACL). See OSS$_ACL_POSITION for more information on explicit access
control list positioning.
OSS$_ACL_DELETE
Deletes all unprotected ACEs in an ACL.
OSS$_ACL_DELETE_ALL
Deletes an entire ACL, including protected ACEs.
OSS$_ACL_DELETE_ENTRY
Deletes an ACE pointed to by the buffer address or, if the buffer
address is specified as 0, the ACE at the current position.
OSS$_ACL_FIND_ENTRY
Locates an ACE pointed to by the buffer address. OSS$_ACL_FIND_ENTRY
sets the position within the ACL for succeeding ACL operations; for
example, for a deletion or modification of the ACE. If the buffer
address is 0, it returns SS$_ACCVIO.
OSS$_ACL_FIND_NEXT
Advances the current position to the next ACE in the ACL.
OSS$_ACL_FIND_TYPE
Returns an ACE of a particular type if there is one in the buffer
pointed to by the buffer address. OSS$_ACL_FIND_TYPE sets the position
within the ACL for succeeding ACL operations. If the buffer address is
0, it returns SS$_ACCVIO.
OSS$_ACL_MODIFY_ENTRY
Replaces an ACE at the current position with the ACE pointed to by the
buffer address.
OSS$_ACL_POSITION_BOTTOM
Sets the ACL position to point to the bottom of the ACL.
OSS$_ACL_POSITION_TOP
Sets the ACL position to point to the top of the ACL.
OSS$_OWNER
Sets the owner UIC of the selected object to the value in the buffer.
The buffer size must be 4 bytes.
OSS$_PROTECTION
Sets the selected object's protection code to the value in the buffer.
The buffer size must be 2 bytes.
Description
The Set Security service modifies the security characteristics of a
protected object. Security characteristics include such information as
the protection code, the owner, and the access control list (ACL).
The security management services, $SET_SECURITY and $GET_SECURITY,
maintain a single master copy of a profile for every protected object
in an OpenVMS Cluster system. They also ensure that only one process at
a time can modify an object's security profile.
When you call $SET_SECURITY, the service performs the following steps:
- It selects the specified protected object.
- It fetches a local copy of the object's security profile, unless
the service is operating on an existing context.
- It modifies the local profile.
- It updates the master copy of the profile if the local flag is
clear and there was no error.
- It deletes the local copy of the profile and returns if RELCTX is
specified or if no context is specified.
There are different ways of identifying which protected object
$SET_SECURITY should process:
- Whenever the contxt argument has a nonzero value,
$SET_SECURITY uses the context to select the object and ignores the
class name, object name, and object handle.
- With some types of objects, such as a file or a device, it is
possible to select an object on the basis of its
objhan and clsnam values.
- When the clsnam and objnam
arguments are provided, $SET_SECURITY uses an object's class name and
object name to select the object.
The context for a security management operation can be established
through either $GET_SECURITY or $SET_SECURITY. Whenever the context is
set by one service, the other service can use it provided the necessary
locks are being held. A caller to $GET_SECURITY needs to set the write
lock flag (OSS$M_WLOCK) to inspect a profile value, maintain the lock
on the object's profile, and then modify some value through a call to
$SET_SECURITY.
There are many situations in which the contxt argument
is essential. By establishing a context for an ACL operation, for
example, a caller can retain an ACL position across calls to
$GET_SECURITY so that a set of ACEs can be read and modified
sequentially. A security context is released by a call to $SET_SECURITY
or $GET_SECURITY that sets the OSS$M_RELCTX flag. Once the context is
deleted, the user-supplied context longword is reset to 0.
Required Access or Privileges
Control access to the object is required.
Required Quota
None
Related Services
$GET_SECURITY
Condition Values Returned
|
SS$_NORMAL
|
The service completed successfully.
|
|
SS$_ACCVIO
|
The parameter cannot be read and the buffer cannot be written.
|
|
SS$_BADPARAM
|
You specified an invalid object, attribute code, or item size.
|
|
SS$_INSFARG
|
The
clsnam and
objnam arguments are not specified, the
clsnam and
objhan arguments are not specified, or the
contxt argument is not specified.
|
|
SS$_INVBUFLEN
|
The buffer size for one of the item codes was invalid.
|
|
SS$_INVCLSITM
|
The item code that you specified is not supported for the class.
|
|
SS$_INVFILFOROP
|
An invalid file name was specified; the file name contained either a
node or wildcard specification.
|
|
SS$_MMATORB
|
The attempted update cannot be performed. The object profile was
changed by another process.
|
|
SS$_NOCLASS
|
The named object class does not exist.
|
|
SS$_OBJLOCKED
|
The selected object is currently write locked.
|
$SET_SYSTEM_EVENT (Alpha and I64)
On Alpha and I64 systems, establishes a request for notification when
an OpenVMS system event occurs.
Format
SYS$SET_SYSTEM_EVENT event ,astadr ,astprm ,acmode ,flags ,handle
C Prototype
int sys$set_system_event (unsigned int event, void
(*astadr)(__unknown_params), int astprm, unsigned int acmode, unsigned
int flags, struct _generic_64 * handle);
Arguments
event
| OpenVMS usage: |
event_code |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Event code indicating the type of system event for which an AST is to
be delivered. The event argument is a value indicating
which type of event is of interest.
Each event type has a symbolic name. The $SYSEVTDEF macro defines the
following symbolic names:
| Symbolic Name |
Description |
|
SYSEVT$C_ADD_MEMBER
|
One or more OpenVMS instances have joined the OpenVMS Galaxy sharing
community.
|
|
SYSEVT$C_DEL_MEMBER
|
One or more OpenVMS instances have left the OpenVMS Galaxy sharing
community.
|
|
SYSEVT$C_ADD_ACTIVE_CPU
|
One or more processors have become active within this OpenVMS instance.
|
|
SYSEVT$C_DEL_ ACTIVE_CPU
|
One or more processors have become inactive within this OpenVMS
instance.
|
|
SYSEVT$C_ADD_CONFIG_CPU
|
One or more CPUs have been added to the set of available CPUs for this
OpenVMS instance.
|
|
SYSEVT$C_DEL_CONFIG_CPU
|
One or more processors have been removed from this OpenVMS instance.
|
|
SYSEVT$C_TDF_CHANGE
|
The system's time differential factor has changed.
|
astadr
| OpenVMS usage: |
ast_procedure |
| type: |
procedure value |
| access: |
call without stack unwinding |
| mechanism: |
by 32-bit or 64-bit reference |
Notification AST routine to receive control after a change in OpenVMS
system configuration occurs.
astprm
| OpenVMS usage: |
user_arg |
| type: |
quadword |
| access: |
read only |
| mechanism: |
by value |
The quadword AST parameter to be passed to the AST routine.
acmode
| OpenVMS usage: |
access_mode |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Access mode at which the system event AST is to execute. The
acmode argument is a longword containing the access
mode.
Each access mode has a symbolic name. The $PSLDEF macro defines the
following symbols for the four access modes.
| Symbolic Name |
Description |
|
PSL$C_KERNEL
|
Kernel
|
|
PSL$C_EXEC
|
Executive
|
|
PSL$C_SUPER
|
Supervisor
|
|
PSL$C_USER
|
User
|
The value of the access mode is maximized with the access mode of the
caller.
flags
Defined in SYSEVTDEF.
|
SYSEVT$M_REPEAT_NOTIFY
|
When this flag is set, event notification is repeated.
|
handle
| OpenVMS usage: |
handle |
| type: |
quadword (unsigned) |
| access: |
read/write |
| mechanism: |
by reference |
The virtual address of a naturally aligned quadword for the event
handle.
Description
The Set System Event service establishes a request for notification
when a system event occurs. It may create a new system event
notification object, add an event to a new or existing object, and
enable notification on a new or existing object.
|
