| Previous | Contents | Index |
This chapter describes the OpenVMS System Code Debugger (SCD) and how it can be used to debug nonpageable system code and device drivers running at any interrupt priority level (IPL).
You can use SCD to perform the following tasks:
The use of SCD requires two systems:
SCD is a symbolic debugger. You can specify variable names, routine names, and so on, precisely as they appear in your source code. SCD can also display the source code where the software is executing, and allow you to step by source line.
SCD recognizes the syntax, data typing, operators, expressions, scoping rules, and other constructs of a given language. If your code or driver is written in more than one language, you can change the debugging context from one language to another during a debugging session.
To use SCD, you must do the following:
The following sections cover these tasks in more detail, describe the
available user-interface options, summarize applicable OpenVMS Debugger
commands, and provide a sample SCD session.
11.1 User-Interface Options
SCD has the following user-interface options:
For more information about using the OpenVMS DECwindows Motif interface
and OpenVMS Debugger commands with SCD, see the HP OpenVMS Debugger Manual.
11.2 Building a System Image to Be Debugged
Debugging optimized code is much more difficult and is not recommended unless you know the Alpha or Integrity server architecture well. The instructions are reordered so much that single-stepping by source line will look like you are randomly jumping all over the code. Also note that you cannot access all variables. SCD reports that they are optimized away. |
$ LINK/EXE=EXE$:MY_EXECLET/DSF=EXE$:MY_EXECLET OPTIONS_FILE/OPT |
The target kernel is controlled by flags and devices specified when the system is booted, by XDELTA commands, by a configuration file, and by several system parameters. The following sections contain more information about these items.
You can specify flags on the boot command line. Boot flags are specified as a hex number; each bit of the number represents a true or false value for a flag. The following flag values are relevant to the system code debugger.
The form of the boot command varies depending on the platform and type OpenVMS system. However, all SCD boot commands have the concept of boot flags, boot device, and dedicated Ethernet device. In all environments, you must specify an Ethernet device on the target system to use to communicate with the host debugger. It is currently a restriction that this device must not be used for anything else (either for booting or network software such as DECnet, TCP/IP products, and LAT products).
To use Alpha SCD, you must specify the Ethernet device with the boot command. In this example, we are using DEC 3000 Model 400 Alpha Workstation syntax. We are booting from the DKB100 disk and using the ESA0 Ethernet device. We are also setting the SCD, XDELTA, and initial (earliest) breakpoint flags:
>>> show device
.
.
.
>>> boot dkb100,esa0 -fl 0,8006
|
You can set these devices and flags to be the default values so that you will not have to specify them each time you boot:
>>> set bootdef_dev dkb100,esa0
>>> set boot_osflags 0,8006
|
To use Integrity server SCD, you can specify an Ethernet device (debug_dev) BEFORE loading the Operating System and AFTER you have selected the device/partition. Setting debug_dev is sticky. That is, you only need to set it once. Using a HP rx2600 syntax:
A sample Integrity server Boot Menu follows.
Please select a boot option
EFI Shell [Built-in]
PESOS - X8.2-AHI (Topaz BL2) on $1$DGA3890:[SYS2.]
PESOS - X8.2-AHI (Topaz BL2) on $1$DGA3890:[SYS2.] sysboot
PESOS - E8.2-ADH (Topaz BL1) on $1$DGA3891:[SYS2.]
PESOS - E8.2-ADH (Topaz BL1) on $1$DGA3891:[SYS2.] sysboot
Boot Option Maintenance Menu
System Configuration Menu
|
Select the EFI Shell [Built-in].
Loading.: EFI Shell [Built-in]
EFI Shell version 1.10 [14.61]
Device mapping table
fs0 : Acpi(HWP0002,100)/Pci(1|0)/Scsi(Pun0,Lun0)/HD(Part1,SigA02952
fs1 : Acpi(HWP0002,300)/Pci(1|0)/Fibre(WWN50001FE10011B15D,Lun2200)
fs2 : Acpi(HWP0002,300)/Pci(1|0)/Fibre(WWN50001FE10011B15D,Lun2200)
fs3 : Acpi(HWP0002,300)/Pci(1|0)/Fibre(WWN50001FE10011B15D,Lun2300)
.
.
.
Shell>
|
Select the desired device/partition:
Shell> fs1:
fs1:\>
|
Use the utilities in \efi\vms. Use vms_show to list the devices and vms_set to set Ethernet device (debug_dev), if necessary.
fs1:\> \efi\vms\vms_show device VMS: EIA0 EFI: Acpi(000222F0,0)/Pci(3|0)/Mac(00306E39F77B) VMS: DKB200 EFI: fs1: Acpi(000222F0,100)/Pci(1|1)/Scsi(Pun2,Lun0) VMS: DKB0 EFI: fs0: Acpi(000222F0,100)/Pci(1|1)/Scsi(Pun0,Lun0) VMS: EWA0 EFI: Acpi(000222F0,100)/Pci(2|0)/Mac(00306E3977C5) . . . |
Set the Ethernet device.
fs1:\> \efi\vms\vms_set debug_dev eia0 VMS: EIA0 0-30-6E-39-F7-CF EFI: Acpi(000222F0,0)/Pci(3|0)/Mac(00306E39F7CF) |
Finally, load the OS. In this example, the boot is with the SCD and initial (earliest) breakpoint flags using root 2 (SYS2), that will vary with system setups.
fs1:\> \efi\vms\vms_loader -flags "2,8004"
|
You can set the flags to be the default value instead of specifying them for each and every OS load:
fs1:\> set vms_flags "2,8004"
|
You can also build the entire boot device, OS load command with flags setting as a Boot Option. See the "Boot Option Maintenance Menu", described in the HP OpenVMS System Manager's Manual, Volume 1: Essentials.
The SCD target system reads a configuration file in SYS$SYSTEM named DBGTK$CONFIG.SYS. The first line of this file contains a default password, which must be specified by the host debug system to connect to the target. The default password may be the null string; in this case the host must supply the null string as the password (/PASSWORD="") on the connect command as described in Section 11.5, or no password at all. Other lines in this file are reserved by HP. Note that you must create this file because HP does not supply it. If this file does not exist prior to booting with SCD enabled, you can only run SCD by specifying a default password with the XDELTA ;R command described in the following section.
When the system is booted with both the XDELTA boot flag and the SCD boot flag, the following two additional XDELTA commands are enabled:
The optional integer argument n controls the behavior of
the ;R command as follows:
| Value of N | Action |
|---|---|
| +1 | Gives control to SCD by simulating a call to INI$BRK |
| +2 | Returns to XDELTA after changing the password. 2;R without a password is a no-op |
| 0 | Performs the default action |
| -1 | Changes the password, breaks any existing connection to SCD, and then simulates a call to INI$BRK (which will wait for a new connection to be established and then give control to SCD) |
| -2 | Returns to XDELTA after changing the password and breaking an existing connection |
| Bit 0 | At the start of INIT |
| Bit 1 | At the end of INIT |
| Bit 2 | At the point in INIT just prior to starting secondary CPUs |
| Bit 3 | If INI$BRK is called from an outer mode |
| Bit 4 | Before calling the initialization routine of a newly-loaded executive image |
| Bits 5-31 | Reserved by HP |
| Bit 0 | Disables system clock |
| Bit 1 | Disables CPU sanity timeouts |
| Bit 2 | Disables CPU spinwait timeouts |
It is always SCD on the host system that initiates a connection to the target kernel. When SCD initiates this connection, the target kernel accepts or rejects the connection based on whether the remote debugger presents it with a node name and password that matches the password in the target system (either the default password from the SYS$SYSTEM:DBGTK$CONFIG.SYS file, or a different password specified via XDELTA). SCD obtains the node name from the SCSNODE system parameter.
The target kernel can accept a connection from SCD any time the system
is running below IPL 22, or if XDELTA is in control (at IPL 31).
However, the target kernel actually waits at IPL 31 for a connection
from the SCD host in two cases: when it has no existing connection to
an SCD host and (1) it receives a breakpoint caused by a call to
INI$BRK (including either of the initial breakpoints), or (2) when you
enter a 1;R or -1;R command to XDELTA.
11.3.2 Interactions Between XDELTA and the Target Kernel/System Code Debugger
XDELTA and the target kernel are integrated into the same system. Normally, you choose to use one or the other. However, XDELTA and the target kernel can be used together. This section explains how they interoperate.
The XDELTA boot flag controls which debugger (XDELTA or the SCD target kernel) gets control first. If it is not set, the target kernel gets control first, and it is not possible to use XDELTA without rebooting. If it is set, XDELTA gets control first, but you can use XDELTA commands to switch to the target kernel and to switch INI$BRK behavior such that the target kernel gets control when INI$BRK is called.
Breakpoints always stick to the debugger that set them; for example, if you set a breakpoint at location "A" with XDELTA, and then you enter the commands 1;K (switch INI$BRK to the system code debugger) and ;R (start using the system code debugger) then, from SCD, you can set a breakpoint at location "B". If the system executes the breakpoint at A, XDELTA reports a breakpoint, and SCD will see nothing (though you could switch to SCD by issuing the XDELTA ;R command). If the system executes the breakpoint at B, SCD will get control and report a breakpoint (you cannot switch to XDELTA from SCD).
Notice that if you examine location A with SCD, or location B with XDELTA, you will see a BPT instruction, not the instruction that was originally there. This is because neither debugger has any information about the breakpoints set by the other debugger.
One useful way to use both debuggers together is when you have a system that exhibits a failure only after hours or days of heavy use. In this case, you can boot the system with SCD enabled (8000), but with XDELTA the default (0002) and with initial breakpoints enabled (0004). When you reach the initial breakpoint, set an XDELTA breakpoint at a location that will only be reached when the error occurs. Then proceed. When the error breakpoint is reached, possibly days later, then you can set up a remote system to debug it and enter the ;R command to XDELTA to switch control to SCD.
Here is another technique to use on Alpha when you do not know where to put an error breakpoint as previously mentioned. Boot the system with only the SCD boot flag set. When you see that the error has occurred, halt the system and initiate an IPL 14 interrupt, as you would to start XDELTA. The target kernel will get control and wait for a connection for SCD.
The equivalent technique on Integrity servers is as follows:
Boot the system with only the SCD flag set (bit 15). When you see that
the error has occurred, type Ctrl/P at the console. This will give
control to XDELTA (even though the XDELTA boot flag is not set) and you
can now type 1;R. The target kernel will get control and wait for a
connection for SCD.
11.3.3 Interactions between the Target Kernel, the System Code Debugger, and other system components
The target kernel must have exclusive use of its Ethernet device. Some
system components, such as DECnet, will not start if the System Code
Debugger is loaded. If there are multiple Ethernet devices, and the
system is configured to give exclusive access of the SCD ethernet
device to the target kernel, the logical name DBGTK$OVERRIDE must be
defined, indicating that the affected system components should start up
as normal. The logical name can either be defined systemwide, or in the
process where the startup command for the system component will be
executed.
11.4 Setting Up the Host System
To set up the host system, you need access to all system images and drivers that are loaded (or can be loaded) on the target system. You should have access to a source listings kit or a copy of the following directories:
SYS$LOADABLE_IMAGES: SYS$LIBRARY: SYS$MESSAGE: |
You need all the .EXE files in those directories. The .DSF files are available with the OpenVMS source listings kit.
Optionally, you need access to the source files for the images to be debugged. SCD will look for the source files in the directory where they were compiled. If your build system and host system are different, you must use the SET SOURCE command to point SCD to the location of the source code files. For an example of the SET SOURCE command, see Section 11.12.
Before making a connection to the target system, you must set up the logical name DBGHK$IMAGE_PATH, which must be set up as a search list to the area where the system images or .DSF files are kept. For example, if the copies are in the following directories:
DEVICE:[SYS$LDR] DEVICE:[SYSLIB] DEVICE:[SYSMSG] |
$ define dbghk$image_path DEVICE:[SYS$LDR],DEVICE:[SYSLIB],DEVICE:[SYSMSG] |
This works well for debugging using all the images normally loaded on a given system. However, you might be using the debugger to test new code in an execlet or a new driver. Because that image is most likely in your default directory, you must define the logical name as follows:
$ define dbghk$image_path [],DEVICE:[SYS$LDR],DEVICE:[SYSLIB],DEVICE:[SYSMSG] |
If SCD cannot find one of the images through this search path, a warning message is displayed. SCD will continue initialization as long as it finds at least two images. If SCD cannot find the SYS$BASE_IMAGE and SYS$PUBLIC_VECTORS files, which are the OpenVMS operating system's main image files, an error message is displayed and the debugger exits.
If and when this happens, check the directory for the image files and
compare it to what is loaded on the target system.
11.5 Starting the System Code Debugger
To start SCD on the host side, enter the following command:
$ DEBUG/KEEP |
SCD displays the DBG> prompt. With the DBGHK$IMAGE_PATH logical name defined, you can invoke the CONNECT command and the optional qualifiers /PASSWORD and /IMAGE_PATH.
To use the CONNECT command and the optional qualifiers (/PASSWORD and /IMAGE_PATH) to connect to the node with name nodename, enter the following command:
DBG> CONNECT %NODE_NAME nodename /PASSWORD="password" |
If a password has been set up on the target system, you must use the /PASSWORD qualifier. If a password is not specified, a zero length string is passed to the target system as the password.
The /IMAGE_PATH qualifier is also optional. If you do not use this qualifier, SCD uses the DBGHK$IMAGE_PATH logical name as the default. The /IMAGE_PATH qualifier is a quick way to change the logical name. However, when you use it, you cannot specify a search list. You can use only a logical name or a device and directory, although the logical name can be a search list.
Usually, SCD obtains the source file name from the object file. This is
put there by the compiler when the source is compiled with the /DEBUG
qualifier. The SET SOURCE command can take a list of paths as a
parameter. It treats them as a search list.
11.6 Summary of System Code Debugger Commands
In general, any OpenVMS debugger command can be used in SCD. For a complete list, refer to the HP OpenVMS Debugger Manual. The following are a few examples:
You can also use the OpenVMS debugger command SDA to examine the target
system with System Dump Analyzer semantics. This command, which is not
available when debugging user programs, is described in the next
section.
11.7 Using System Dump Analyzer Commands
Once a connection has been established to the target system, you can use the commands listed in the previous section to examine the target system. You can also use some System Dump Analyzer (SDA) commands, such as SHOW SUMMARY and SHOW DEVICE. This feature allows the system programmer to take advantage of the strengths of both the OpenVMS Debugger and SDA to examine the state of the target system and to debug system programs such as device drivers.
To obtain access to SDA commands, you simply type "SDA" at the OpenVMS Debugger prompt ("DBG>") at any time after a connection has been established to the target system. SDA initializes itself and then outputs the "SDA>" prompt. Enter SDA commands as required. (See Chapter 4 for more information.) To return to the OpenVMS Debugger, you enter "EXIT" at the "SDA>" prompt. Optionally, you may invoke SDA to perform a single command and then return immediately to the OpenVMS Debugger, as in the following example:
DBG>SDA SHOW SUMMARY |
You may reenter SDA at any time, with or without the optional SDA command. Once SDA has been initialized, the SDA> prompt is output more quickly on subsequent occasions.
Note that there are some limitations on the use of SDA from within SCD.
The SCD host and the target kernel use a private Ethernet protocol to communicate. The best way to ensure that the two systems can see each other is for them both to be on the same Ethernet segment. Otherwise, your network and its bridges must be set up to pass through the packets with the protocol 08-00-2B-80-4B and multicast address 09-00-2B-02-01-0F.
The network portion of the target system uses the specified Ethernet
device and communicates through it. The network portion of the host
system finds the first Ethernet device and communicates through it. If
the host SCD picks the wrong device for your needs, then you can force
it to use the correct device by defining the logical DBGHK$ADAPTOR as
the template device name for the appropriate adaptor.
11.9 Troubleshooting Checklist
If you have trouble starting a connection, perform the following tasks to correct the problem:
There are three possible network errors:
The netfail error message has a status code that can be one of the following values:
| Value | Status |
|---|---|
| 2, 4, 6 | Internal network error, submit a problem report to HP. |
| 8,10,14,16,18,20,26,28,34,38 | Network protocol error, submit a problem report to HP. |
| 22,24 | Too many errors on the network device most likely due to congestion. Reduce the network traffic or switch to another network backbone. |
| 30 | Target system scratch memory not available. Check DBGTK_SCRATCH. If increasing this value does not help, submit a problem report to HP. |
| 32 | Ran out of target system scratch memory. Increase value of DBGTK_SCRATCH. |
| All others | There should not be any other network error codes printed. If one occurs that does not match the previous ones, submit a problem report to HP. |
Accessing OpenVMS executive images' symbols is not always
straightforward with SCD. Only a subset of the symbols may be
accessible at one time and in some cases, the symbol value the debugger
currently has may be stale. To understand these problems and their
solutions, you must understand how the debugger maintains its symbol
tables and what symbols exist in the OpenVMS executive images. The
following sections briefly summarize these topics.
11.11.1 Overview of How the OpenVMS Debugger Maintains Symbols
The debugger can access symbols from any image in the OpenVMS loaded system image list by reading in either the .DSF or .EXE file for that particular image. The .EXE file contains information only about symbols that are part of the symbol vector for that image. The current image symbols for any set module are defined. (You can tell if you have the .DSF or .EXE file by doing a SHOW MODULE. If there are no modules, you have the .EXE file.) This includes any symbols in the SYS$BASE_IMAGE.EXE symbol vector for which the code or data resides in the current image. However, you cannot access a symbol that is part of the SYS$BASE_IMAGE.EXE symbol vector that resides in another image.
In general, at any one point in time, the debugger can access only the symbols from one image. It does this to reduce the time it takes to search for a symbol in a table. To load the symbols for a particular image, use the SET IMAGE command. When you set an image, the debugger loads all the symbols from the new image and makes that image the current image. The symbols from the previous image are in memory, but the debugger will not look through them to translate symbols.
There is a set of modules for each image the debugger accesses. The symbol tables in the image that are part of these modules are not loaded with the SET IMAGE command. Instead they can be loaded with the SET MODULE <module-name> or SET MODULE/ALL commands. As they are loaded, a new symbol table is created in memory under the symbol table for the image. Figure 11-1 shows what this looks like.
Figure 11-1 Maintaining Symbols
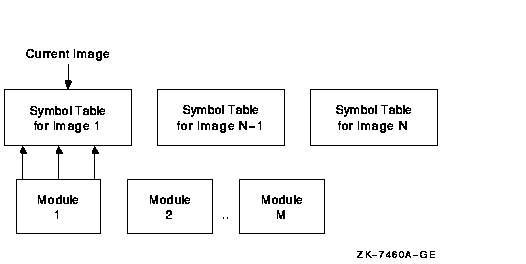
When the debugger needs to look up a symbol name, it first looks at the current image to find the information. If it does not find it there, it then looks into the appropriate module. It determines which module is appropriate by looking at the module range symbols which are part of the image symbol table.
To see the symbols that are currently loaded, use the debugger's SHOW
SYMBOL command. This command has a few options to obtain more than just
the symbol name and value. (See the HP OpenVMS Debugger Manual for more details.)
11.11.2 Overview of OpenVMS Executive Image Symbols
Depending on whether the debugger has access to the .DSF or .EXE file, different kinds of symbols could be loaded. Most users will have the .EXE file for the OpenVMS executive images and a .DSF file for their private images---that is, the images they are debugging.
The OpenVMS executive consists of two base images, SYS$BASE_IMAGE.EXE and SYS$PUBLIC_VECTORS.EXE, and a number of separately loadable executive images.
The two base images contain symbol vectors. For SYS$BASE_IMAGE.EXE, the symbol vector is used to define symbols accessible by all the separately loadable images. This allows these images to communicate with each other through cross-image routine calls and memory references. For SYS$PUBLIC_VECTORS.EXE, the symbol vector is used to define the OpenVMS system services. Because these symbol vectors are in the .EXE and the .DSF files, the debugger can load these symbols no matter which one you have.
All images in the OpenVMS executive also contain global and local
symbols. However, none of these symbols ever gets into the .EXE file
for the image. These symbols are put in the specific module's section
of the .DSF file if that module was compiled using /DEBUG and the image
was linked using /DSF.
11.11.3 Possible Problems You May Encounter
Access to All Executive Image Symbols
When the current image is not SYS$BASE_IMAGE, but one of the separately loaded images, the debugger does not have access to any of the symbols in the SYS$BASE_IMAGE symbol vector. This means you cannot access (set breakpoints, and so on) any of the cross-image routines or data cells. The only symbols you have access to are the ones defined by the current image.
If the debugger has access only to the .EXE file, then only symbols that have vectors in the base image are accessible. For .DSF files, the current image symbols for any set module are defined. (You can tell if you have the .DSF or .EXE by using the SHOW MODULE command---if there are no modules you have the .EXE). This includes any symbols in the SYS$BASE_IMAGE.EXE symbol vector for which the code or data resides in the current image. However, the user cannot access a symbol that is part of the SYS$BASE_IMAGE.EXE symbol vector that resides in another image. For example, if you are in one image and you want to set a breakpoint in a cross-image routine from another image, you do not have access to the symbol. Of course, if you know in which image it is defined, you can do a SET IMAGE, SET MODULE/ALL, and then a SET BREAK.
There is a debugger workaround for this problem. The debugger and SCD let you use the SET MODULE command on an image by prefixing the image name with SHARE$ (SHARE$SYS$BASE_IMAGE, for example). This treats that image as a module which is part of the current image. In the previous figure, think of it as another module in the module list for an image. Note, however, that only the symbols for the symbol vector are loaded. None of the symbols for the modules of the SHARE$xxx image are loaded. Therefore, this command is only useful for base images.
So, in other words, by doing SET MODULE SHARE$SYS$BASE_IMAGE, the debugger gives you access to all cross-image symbols for the OpenVMS executive.
| Previous | Next | Contents | Index |