HP OpenVMS Guide to System Security: OpenVMS Version 8.4 > Chapter 14 Using Protected Subsystems

Example of a Protected Subsystem
R. D. Taylor Inc., a company specializing in building
supplies, decides to set up a protected subsystem for its purchasing
and accounts payable departments. Although the departments are in
different parts of the company, they share a common database for recording
purchases from suppliers. When the company's inventory drops below
the desired level, the purchasing department is directed to order
required supplies. Purchasing personnel find suppliers (if necessary),
assign purchase order numbers, and issue a purchase orders. When the goods arrive, the receiving and quality
control departments check the contents against what was ordered, ensure
the goods meet quality standards, and put the goods into inventory.
Once the shipment is processed, the information goes to the accounts
payable department, which settles the invoices. Administrators in the accounts payable department
check the invoices against purchase orders and run a payments program
to calculate the monies due to suppliers each week. Payments are recorded
in a database, and checks are printed on a printer loaded with company
checks. Using the subsystem lets the company meet two
objectives: It gives purchasing personnel
the right to reference or record purchase orders in the company database,
and it gives personnel in the accounts payable department the right
to verify suppliers' invoices. Purchasing personnel with these
tasks hold the SUPPLIERS_ORDERS identifier. Accounts payable personnel
hold the ACCOUNTS_PAYABLE identifier. These
employees run ORDERS.EXE to update the supplier information. The program
stores data in ORDERS.DAT. It gives trusted administrators
in the accounts payable department the right to update databases,
calculate payments due, and print checks. (One printer, loaded with
company checks, is used for this purpose.) These administrators hold
the ACCOUNTS_PAYABLE identifier. The administrators
run PAYMENTS.EXE to perform these tasks. The program records payments
made in the data file PAYMENTS.DAT.
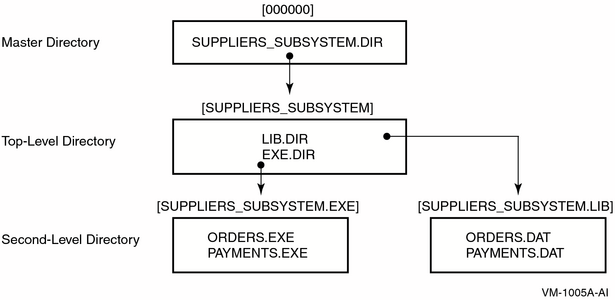
The company appoints one employee, McGrey, to
design and manage the subsystem. “Directory Structure of the Taylor Company's Subsystem” illustrates the directory structure
of the Taylor subsystem, and “Subsystem Command Procedure” shows the command procedure McGrey
wrote to implement it. Protecting the Top-Level Directory |  |
McGrey implements a directory structure in which
users can gain access to the subsystem only by holding an appropriate
identifier: purchasing personnel hold the identifier SUPPLIERS_ORDERS,
and the accounts payable administrators hold the identifier ACCOUNTS_PAYABLE.
As subsystem manager, McGrey holds the identifier SUPPLIERS_SUBSYSTEM. The top-level directory SUPPLIERS_SUBSYSTEM.DIR
has the protection shown in the following example. Example 14-2 Protection of SUPPLIERS_SUBSYSTEM.DIR
$DIRECTORY/SECURITY SYS$SYSDEVICE:[000000]SUPPLIERS_SUBSYSTEM.DIR
|
Directory SYS$SYSDEVICE:[000000]
SUPPLIERS_SUBSYSTEM.DIR;1
SUPPLIERS_SUBSYSTEM (RWE,RWE,,)
[1]
(CREATOR,ACCESS=NONE)
[2]
(DEFAULT_PROTECTION,SYSTEM:RWED,OWNER:RWED,GROUP:,WORLD:)
[3]
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL)
[4]
(IDENTIFIER=SUPPLIERS_ORDERS,ACCESS=EXECUTE)
[5]
(IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE)
[6]
(IDENTIFIER=*,ACCESS=NONE) [7]
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,
OPTIONS=DEFAULT,ACCESS=READ+WRITE+CONTROL)
[8]
(IDENTIFIER=SUPPLIERS_ORDERS,OPTIONS=DEFAULT,ACCESS=EXECUTE)
(IDENTIFIER=ACCOUNTS_PAYABLE,OPTIONS=DEFAULT,ACCESS=EXECUTE)
(IDENTIFIER=*,OPTIONS=DEFAULT,ACCESS=NONE)
Total of 1 file. |
 |
The directory's protection
code gives read, write, and execute access to users in the system
and owner categories but no access to group or world users. Therefore,
group and world users have to gain access through the ACL. A Creator ACE ensures
that users creating files in this directory have no special access
to them. (See “Setting Defaults for a Directory Owned by a Resource Identifier” for information on Creator ACEs.) A Default Protection ACE
denies group and world users access to files created in directory. McGrey holds the subsystem
identifier SUPPLIERS_SUBSYSTEM. This ACE gives McGrey read, write,
and control access so McGrey can manage the subsystem directories
and images. Holders of the SUPPIERS_ORDERS
identifier have execute access so they can access files in subdirectories. Holders of the ACCOUNTS_PAYABLE
identifier have execute access so they can access files in subdirectories. Users holding any other
identifiers have no access. McGrey added the Default
attribute to all Identifier ACEs and includes them here so all Identifier
ACEs are propagated to subdirectory ACLs.
Protecting Subsystem Directories |  |
The directory EXE.DIR has the same protection
as the top-level directory because subsystem users need to access
the subsystem images: ORDERS.EXE and PAYMENTS.EXE. The other directory,
LIB.DIR, is more restricted because only the subsystem images and
McGrey need access. Example 14-3 Protection of SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM] $DIRECTORY/SECURITY SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM...] |
 |
 |
Directory SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM]
EXE.DIR;1 SUPPLIERS_SUBSYSTEM (RWE,RWE,,)
[1]
(CREATOR,ACCESS=NONE)
(DEFAULT_PROTECTION,SYSTEM:RWED,OWNER:RWED,GROUP:,WORLD:)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL)
(IDENTIFIER=SUPPLIERS_ORDERS,ACCESS=EXECUTE)
(IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE)
(IDENTIFIER=*,ACCESS=NONE)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,OPTIONS=DEFAULT,
ACCESS=READ+WRITE+CONTROL)
(IDENTIFIER=SUPPLIERS_ORDERS,OPTIONS=DEFAULT,ACCESS=EXECUTE)
(IDENTIFIER=ACCOUNTS_PAYABLE,OPTIONS=DEFAULT,ACCESS=EXECUTE)
(IDENTIFIER=*,OPTIONS=DEFAULT,ACCESS=NONE)
LIB.DIR;1 SUPPLIERS_SUBSYSTEM (RWE,RWE,,)
[2]
(CREATOR,ACCESS=NONE)
(DEFAULT_PROTECTION,SYSTEM:RWED,OWNER:RWED,GROUP:,WORLD:)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL)
(IDENTIFIER=*,ACCESS=NONE)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,OPTIONS=DEFAULT,
ACCESS=READ+WRITE+CONTROL)
(IDENTIFIER=*,OPTIONS=DEFAULT,ACCESS=NONE)
Total of 2 files.
[vellip] |
 |
[SUPPLIERS_SUBSYSTEM.EXE]
has the same protection code and ACL as the parent directory shown
in “Protecting the Top-Level Directory”. Subsystem
users need to run programs stored in this directory. [SUPPLIERS_SUBSYSTEM.LIB]
has the same protection code but a more restrictive ACL because only
the subsystem manager and the subsystem images need access.
Protecting the Images and Data Files |  |
As the following example shows, the necessary
company personnel can access the subsystem's images, ORDERS.EXE
and PAYMENTS.EXE, but only the images can update the data files. Example 14-4 Access to Subsystem's Images ORDERS.EXE and PAYMENTS.EXE Directory SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM.EXE]
ORDERS.EXE;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,) [1]
(SUBSYSTEM,IDENTIFIER=SUPPLIERS_SUBSYSTEM,
ATTRIBUTES=RESOURCE)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,
ACCESS=READ+WRITE+CONTROL)
(IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE)
(IDENTIFIER=*,ACCESS=NONE)
PAYMENTS.EXE;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,) [2]
SUBSYSTEM,IDENTIFIER=SUPPLIERS_SUBSYSTEM,
ATTRIBUTES=RESOURCE)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,
ACCESS=READ+WRITE+CONTROL)
(IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE)
(IDENTIFIER=*,ACCESS=NONE)
Total of 2 files.
Directory SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM.LIB] [3]
ORDERS.DAT;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,
ACCESS=READ+WRITE)
(IDENTIFIER=*,ACCESS=NONE)
PAYMENTS.DAT;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,
ACCESS=READ+WRITE)
(IDENTIFIER=*,ACCESS=NONE)
Total of 2 files.
Grand total of 3 directories, 6 files. |
 |
All subsystem users, those
holding the SUPPLIERS_ORDERS or ACCOUNTS_PAYABLE identifier, can run
ORDERS.EXE. Only subsystem images
and holders of the ACCOUNTS_PAYABLE identifier can run PAYMENTS.EXE. The data files for the
subsystem reside in [SUPPLIERS_SUBSYSTEM.LIB]. Only the subsystem
images and McGrey can access them.
Protecting the Printer |  |
The print queue for checks needs equal protection.
Access is restricted to trusted administrators because they are the
only ones who hold both the subsystem and the ACCOUNTS_PAYABLE identifiers. “Queue Protection” shows
that the queue is protected in such a way that only the trusted administrators
can queue jobs to the printer: Example 14-5 Queue Protection $SHOW SECURITY/CLASS=QUEUE TTA1
|
TTA1 object of class QUEUE
Owner: [SYSTEM]
Protection: (System: M, Owner: D, Group, World)
Access Control List:
(IDENTIFIER=SUPPLIERS_SUBSYSTEM+ACCOUNTS_PAYABLE,-
ACCESS=READ+SUBMIT+MANAGE+DELETE)
(IDENTIFIER=*,ACCESS=NONE) |
Command Procedure for Building the Subsystem |  |
“Subsystem Command Procedure” shows the command procedure used
to create the R. D. Taylor subsystem. Example 14-6 Subsystem Command Procedure  |
$ SET NOON
$ OLD_PRIV = F$SETPRV("NOALL,SYSPRV,CMKRNL,OPER")
$ OLD_DEFAULT = F$ENVIRONMENT("DEFAULT")
$
$ ON CONTROL_Y THEN GOTO LEAVE
$
$ IF P1 .EQS. "REMOVE" THEN GOTO CLEANUP
$ IF P1 .EQS. "VERIFY" THEN SET VERIFY
$!
$! Create the subsystem identifier and the identifiers for personnel
$! performing two different tasks.
$!
$ SET DEFAULT SYS$SYSTEM
$ RUN AUTHORIZE
ADD/IDENTIFIER SUPPLIERS_SUBSYSTEM/ATTRIBUTES=(RESOURCE,SUBSYSTEM)
ADD/IDENTIFIER SUPPLIERS_ORDERS
ADD/IDENTIFIER ACCOUNTS_PAYABLE
!
! Grant the subsystem identifier to the subsystem manager: McGrey.
!
GRANT/IDENTIFIER SUPPLIERS_SUBSYSTEM MCGREY/ATTRIBUTE=(RESOURCE,SUBSYSTEM)
$!
$! Set up the print queue.
$!
$ INITIALIZE/QUEUE/START TTA1
$ SET SECURITY/ACL=(-
(ID=SUPPLIERS_SUBSYSTEM+ACCOUNTS_PAYABLE,ACCESS=READ+SUBMIT+MANAGE+DELETE), -
(ID=*,ACCESS=NONE) )/PROTECTION=(G,W)/CLASS=QUEUE TTA1:
$!
$! Create the directory root to hold the subsystem.
$!
$!
$! Assume that we logged in as McGrey.
$!
$ SET RIGHTS_LIST/ENABLE SUPPLIERS_SUBSYSTEM/ATTRIBUTE=(RESOURCE,SUBSYSTEM)
$ SET DEFAULT SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM]
$!
$! Create the directories for the images and the data files.
$!
$ CREATE/DIR [SUPPLIERS_SUBSYSTEM.EXE]/PROTECTION=(G,W)
$ CREATE/DIR [SUPPLIERS_SUBSYSTEM.LIB]/PROTECTION=(G,W)
$ SET SECURITY/ACL=( (ID=SUPPLIERS_ORDERS,ACCESS=EXECUTE), -
(ID=ACCOUNTS_PAYABLE,ACCESS=EXECUTE), -
(ID=SUPPLIERS_ORDERS,OPTIONS=DEFAULT,ACCESS=EXECUTE), -
(ID=ACCOUNTS_PAYABLE,OPTIONS=DEFAULT,ACCESS=EXECUTE) )/DELETE -
[SUPPLIERS_SUBSYSTEM]LIB.DIR
$!
$! Emulate the creation of the subsystem images.
$!
$ SET DEFAULT [.EXE]
$ CREATE ORDERS.MAR
.ENTRY START,0
$setpri_s pri=#0
10$: BRB 10$
ret
.END START
$ MACRO ORDERS
$ LINK ORDERS
$ SET SECURITY/PROTECTION=(W:RWED) ORDERS.MAR;*,.OBJ;*
$ DELETE ORDERS.MAR;*,.OBJ;*
$ COPY ORDERS.EXE PAYMENTS.EXE
$!
$! Apply the appropriate protection to the images.
$!
$ SET SECURITY/ACL=(ID=SUPPLIERS_ORDERS,ACCESS=EXECUTE)/DELETE PAYMENTS.EXE
$ SET SECURITY/ACL=(SUBSYSTEM,ID=SUPPLIERS_SUBSYSTEM,ATTRIBUTES=RESOURCE) ORDERS.EXE
$ SET SECURITY/ACL=(SUBSYSTEM,ID=SUPPLIERS_SUBSYSTEM,ATTRIBUTES=RESOURCE) PAYMENTS.EXE
$!
$! Create and protect the data files used by the applications.
$!
$ SET DEFAULT [-.LIB]
$ CREATE ORDERS.DAT
$ CREATE PAYMENTS.DAT
$ SET SECURITY/ACL=( (ID=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE), -
(ID=*,ACCESS=NONE) ) ORDERS.DAT
$ SET SECURITY/LIKE=(NAME=ORDERS.DAT) PAYMENTS.DAT
$!
$! Show the directory structure and the queue protection.
$!
$ SET DEFAULT 'OLD_DEFAULT'
$ DEFINE SYS$OUTPUT SUBSYS.LIS
$ DIRECTORY/SECURITY SYS$SYSDEVICE:[000000]SUPPLIERS_SUBSYSTEM.DIR
$ DIRECTORY/SECURITY SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM...]
$ SHOW SECURITY/CLASS=QUEUE TTA1
$ DEASSIGN SYS$OUTPUT
$
$ LEAVE:
$ IF P1 .EQS. "VERIFY" THEN SET NOVERIFY
$ SET DEFAULT 'OLD_DEFAULT'
$ SET PROC/PRIV=('OLD_PRIV')
$ EXIT
$
$ CLEANUP:
$ SET PROC/PRIV=BYPASS
$ SET DEFAULT SYS$SYSDEVICE:[000000]
$ DELETE [SUPPLIERS_SUBSYSTEM...]*.*.*
$ DELETE [SUPPLIERS_SUBSYSTEM]EXE.DIR;
$ DELETE [SUPPLIERS_SUBSYSTEM]LIB.DIR;
$ DELETE SUPPLIERS_SUBSYSTEM.DIR;
$ STOP/QUE/NEXT TTA1
$ DELETE/QUEUE TTA1
$ GOTO LEAVE
|
 |
|