| Previous | Contents | Index |
The following built-in symbols enable you to specify program locations and the current value of an entity:
| Symbol | Description |
|---|---|
|
%CURLOC
. (period) |
Current logical entity---the program location last referenced by an EXAMINE, DEPOSIT, or EVALUATE/ADDRESS command. |
|
%NEXTLOC
Return key |
Logical successor of the current entity---the program location that logically follows the location last referenced by an EXAMINE, DEPOSIT, or EVALUATE/ADDRESS command. Because the Return key is a command terminator, it can be used only where a command terminator is appropriate (for example, immediately after EXAMINE, but not immediately after DEPOSIT or EVALUATE/ADDRESS). |
|
%PREVLOC
^ (circumflex) |
Logical predecessor of current entity---the program location that logically precedes the location last referenced by an EXAMINE, DEPOSIT, or EVALUATE/ADDRESS command. |
|
%CURVAL
\ (backslash) |
Value last displayed by an EVALUATE or EXAMINE command, or deposited by a DEPOSIT command. These two symbols are not affected by an EVALUATE/ADDRESS command. |
In the following example, the variable WIDTH is examined; the value 12 is then deposited into the current location (WIDTH); this is verified by examining the current location:
DBG> EXAMINE WIDTH MOD\WIDTH: 7 DBG> DEPOSIT . = 12 DBG> EXAMINE . MOD\WIDTH: 12 DBG> EXAMINE %CURLOC MOD\WIDTH: 12 DBG> |
In the next example, the next and previous locations in an array are examined:
DBG> EXAMINE PRIMES(4) MOD\PRIMES(4): 7 DBG> EXAMINE %NEXTLOC MOD\PRIMES(5): 11 DBG> EXAMINE [Return] ! Examine next location MOD\PRIMES(6): 13 DBG> EXAMINE %PREVLOC MOD\PRIMES(5): 11 DBG> EXAMINE ^ MOD\PRIMES(4): 7 DBG> |
Note that using the Return key to signify the logical successor does
not apply to all contexts. For example, you cannot press the Return key
after typing the command DEPOSIT to indicate the next location, but you
can always use the symbol %NEXTLOC for that purpose.
B.3.7 Using Symbols and Operators in Address Expressions
The following list describes the symbols and operators that you can use in address expressions. A unary operator has one operand. A binary operator has two operands.
The following examples show the use of built-in symbols and operators in address expressions.
The following command sets a tracepoint at line 26 of the module in which execution is currently suspended:
DBG> SET TRACE %LINE 26 |
The next command displays the source line associated with line 47:
DBG> EXAMINE/SOURCE %LINE 47
module MAIN
47: procedure SWAP(X,Y: in out INTEGER) is
DBG>
|
The next command sets a breakpoint at label 10 of module MOD4:
DBG> SET BREAK MOD4\%LABEL 10 |
The following command displays the value of the variable COUNT that is declared in routine ROUT2 of module MOD4. The backslash (\) pathname delimiter separates the pathname elements:
DBG> EXAMINE MOD4\ROUT2\COUNT MOD4\ROUT2\COUNT: 12 DBG> |
The following command sets a breakpoint on line 26 of the module QUEUMAN:
DBG> SET BREAK QUEUMAN\%LINE 26 |
The following command displays the value of the global symbol X:
DBG> EXAMINE \X |
The order in which the debugger evaluates the elements of an address expression is similar to that used by most programming languages. The order is determined by the following three factors, listed in decreasing order of precedence (first listed have higher precedence):
The debugger operators are listed in decreasing order of precedence as follows:
For example, when evaluating the following expression, the debugger first adds the operands within parentheses, then divides the result by 4, then subtracts the result from 5:
5-(T+5)/4 |
The following command displays the value contained in the memory
location
X + 4 bytes:
DBG> EXAMINE X + 4 |
The following examples show the use of the contents-of operator. In the first example, the instruction at the current PC value is obtained (the instruction whose address is contained in the PC and which is about to execute):
DBG> EXAMINE .%PC MOD\%LINE 5: PUSHL S^#8 DBG> |
In the next example, the source line at the PC value one level down the call stack is obtained (at the call to routine SWAP):
DBG> EXAMINE/SOURCE .1\%PC module MAIN MAIN\%LINE 134: SWAP(X,Y); DBG> |
For the next example, the value of the pointer variable PTR is 7FF00000 hexadecimal, the address of an entity that you want to examine. The value of this entity is 3FF00000 hexadecimal. The following command shows how to examine the entity:
DBG> EXAMINE/LONG .PTR 7FF00000: 3FF00000 DBG> |
In the next example, the contents-of operator (at sign or period) is used with the current location operator (period) to examine a linked list of three quadword-integer pointer variables (identified as L1, L2, and L3 in the following figure). P is a pointer to the start of the list. The low longword of each pointer variable contains the address of the next variable; the high longword of each variable contains its integer value (8, 6, and 12, respectively).
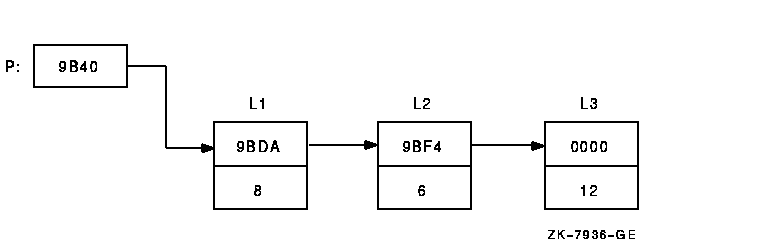
DBG> SET TYPE QUADWORD; SET RADIX HEX
DBG> EXAMINE .P ! Examine the entity whose address
! is contained in P.
00009BC2: 00000008 00009BDA ! High word has value 8, low word
! has address of next entity (9BDA).
DBG> EXAMINE @. ! Examine the entity whose address
! is contained in the current entity.
00009BDA: 00000006 00009BF4 ! High word has value 6, low word
! has address of next entity (9BF4).
DBG> EXAMINE .. ! Examine the entity whose address
! is contained in the current entity.
00009BF4: 0000000C 00000000 ! High word has value 12 (dec.), low word
! has address 0 (end of list).
|
The following example shows how to use the bit-field operator. For example, to examine the address expression X_NAME starting at bit 3 with a length of 4 bits and no sign extension, enter the following command:
DBG> EXAMINE X_NAME <3,4,0> |
The following built-in symbols enable you to obtain information about the current exception and use that information to qualify breakpoints or tracepoints:
| Symbol | Description |
|---|---|
| %EXC_FACILITY | Name of facility that issued the current exception |
| %EXC_NAME | Name of current exception |
| %ADAEXC_NAME | Ada exception name of current exception (for Ada programs only) |
| %EXC_NUMBER | Number of current exception |
| %EXC_SEVERITY | Severity code of current exception |
For example:
DBG> EVALUATE %EXC_NAME "FLTDIV_F" DBG> SET BREAK/EXCEPTION WHEN (%EXC_NAME = "FLTDIV_F") . . . DBG> EVALUATE %EXC_NUMBER 12 DBG> EVALUATE/CONDITION_VALUE %EXC_NUMBER %SYSTEM-F-ACCVIO, access violation at PC !XL, virtual address !XL DBG> SET BREAK/EXCEPTION WHEN (%EXC_NUMBER = 12) |
The conditional expressions in the WHEN clauses are language-specific.
B.3.9 Specifying the Current, Next, and Previous Scope on the Call Stack
You can use the following built-in symbols to obtain and manipulate the scope for symbol lookup and for source or instruction display relative to the routine call stack:
| Built-in Symbol | Description |
|---|---|
| %CURRENT_SCOPE_ENTRY | The call frame that the debugger is currently using as reference when displaying source code or decoded instructions, or when searching for symbols. By default, this is call frame 0. |
| %NEXT_SCOPE_ENTRY | The next call frame down the call stack from the call frame denoted by %CURRENT_SCOPE_ENTRY. |
| %PREVIOUS_SCOPE_ENTRY | The next call frame up the call stack from the call frame denoted by %CURRENT_SCOPE_ENTRY. |
These symbols return integer values that denote a call frame on the call stack. Call frame 0 denotes the routine at the top of the stack, where execution is suspended. Call frame 1 denotes the calling routine, and so on.
For example, the following command specifies that the debugger search for symbols starting with the scope denoted by the next routine down the call stack (rather than starting with the routine at the top of the call stack):
DBG> SET SCOPE/CURRENT %NEXT_SCOPE_ENTRY |
The OpenVMS Debugger supports languages on Integrity servers and Alpha systems.
On Integrity server systems, you can use the debugger with programs written in the following HP languages:
| Ada 1 | Assembler (IAS) | BASIC | BLISS |
| C | C++ | COBOL | Fortran |
| MACRO-32 2 | IMACRO | Pascal |
| HP-Ada | BASIC | BLISS | C |
| C++ | COBOL | Fortran | MACRO-32 1 |
| MACRO-64 | Pascal | PL/I |
The debugger recognizes the syntax, data typing, and scoping rules of each language. It also recognizes each language's operators and expression syntax. Therefore, when using debugger commands you can specify variables and other program entities as you might in the source code of the program. You can also compute the value of a source-language expression using the syntax of that language.
This appendix describes debugging techniques that are common to most of the supported languages. The help topics provide further information specific to each language:
For more information about language-specific debugger support, refer to the documentation furnished with a particular language.
If your program is written in more than one language, you can change the debugging context from one language to another during a debugging session. Use the SET LANGUAGE command with the keyword corresponding to your language choice.
On Integrity servers, you can specify one of the following keywords:
| AMACRO | BASIC | BLISS | C |
| C++ | COBOL | Fortran | PASCAL |
| UNKNOWN |
On Alpha systems, you can specify one of the following keywords:
| ADA | AMACRO | BASIC | BLISS |
| C | C++ | COBOL | FORTRAN |
| MACRO | MACRO64 | PASCAL | UNKNOWN |
When you are debugging a program written in an unsupported language,
enter the SET LANGUAGE UNKNOWN command. To maximize the usability of
the debugger with unsupported languages, this setting causes the
debugger to accept a large set of data formats and operators, including
some that might be specific to only a few supported languages. For
information about the operators and constructs that are recognized when
the language is set to UNKNOWN, type Help Language_UNKNOWN.
C.2 GNAT Ada (Integrity servers only)
The GNAT Pro (Ada 95) compiler is supported on OpenVMS for Integrity server systems. For information on this product, contact Adacore directly.
HP is not porting the HP Ada (Ada 83) compiler from OpenVMS Alpha to OpenVMS for Integrity servers. |
Integrity servers use GNAT Pro Ada 95 from AdaCore Technologies, Inc. For information about this product, see the following online documents from AdaCore:
http://www.gnat.com/wp-content/files/auto_update/gnat-unw-docs/html/gnat_ugn.html |
http://www.gnat.com/wp-content/files/auto_update/gnat-unw-docs/html/gnat_rm.html |
For information about HP Ada on OpenVMS Alpha, see Section C.3.
C.3 HP Ada (Alpha)
The following subtopics describe debugger support for HP Ada on Alpha
systems. For information specific to Ada tasking programs, see also
Chapter 16.
C.3.1 Ada Names and Symbols
The following subtopics describe debugger support for Ada names and symbols, including predefined attributes.
Note that parts of names may be language expressions---for example, attributes such as 'FIRST or 'POS. This affects how you use the EXAMINE, EVALUATE, and DEPOSIT commands with such names. For examples of enumeration types, type Help Specifying_Attributes_with_Enumeration_Types.
C.3.1.1 Ada Names
Supported Ada names follow:
| Kind of Name | Debugger Support |
|---|---|
| Lexical elements |
Full support for Ada rules for the syntax of identifiers.
Function designators that are operator symbols (for example, + and *) rather than identifiers must be prefixed with %NAME. Also, the operator symbol must be enclosed in quotation marks. Full support for Ada rules for numeric literals, character literals, string literals, and reserved words. The debugger accepts signed integer literals in the range --2147483648 to 2147483647. Depending on context and architecture, the debugger interprets floating-point types as F_floating, D_floating, G_floating, H_floating, S_floating, or T_floating. |
| Indexed components | Full support. |
| Slices |
You can examine and evaluate an entire slice or an indexed component of
a slice.
You can deposit only to an indexed component of a slice. You cannot deposit an entire slice. |
| Selected components | Full support, including use of the keyword all in .all. |
| Literals | Full support, including the keyword null. |
| Boolean symbols | Full support (TRUE, FALSE). |
| Aggregates | You can examine the entire record and array objects with the EXAMINE command. You can deposit a value in a component of an array or record. You cannot use the DEPOSIT command with aggregates, except to deposit character string values. |
| Previous | Next | Contents | Index |