How Protected Subsystems Work
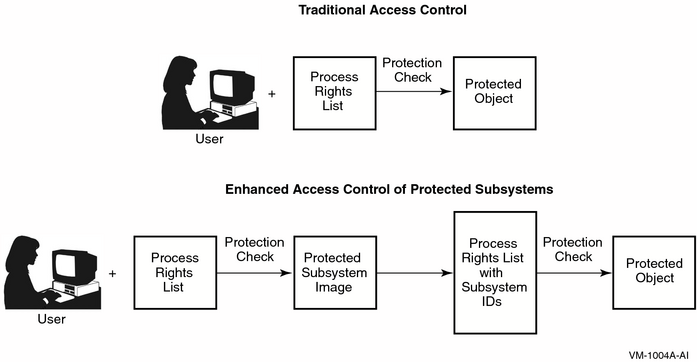
A protected subsystem is an application that, when run, causes the process running the application to be granted one or more identifiers. For as long as a user runs the subsystem, the user's process rights list carries these additional identifiers. “How Protected Subsystems Differ from Normal Access Control” shows how a protected subsystem adds a second level of access control to traditional controls.
Users with execute access to the application gain access to the subsystem. Once in the subsystem, users can work with the data files and other resources of the subsystem.
A subsystem can have several identifiers because the resources consumed by the subsystem (the files, printers, and so forth) can be protected differently.
Possession of subsystem identifiers is limited to the period users are executing the application. Once the users exit from the application, the identifiers are removed from their process rights lists. Subsystem identifiers are also removed from the rights list whenever users enter a Ctrl/Y sequence or attempt to create a subprocess with the DCL command SPAWN. (In this respect, use of the subsystem identifiers is identical to the operation of images installed with privileges.)
The following identifiers are reserved for use in the security subsystem and should not be granted to any user: