HP OpenVMS Systems Documentation |
OpenVMS Guide to System Security
Chapter 13
|
$ SET DEFAULT SYS$SYSTEM $ RUN AUTHORIZE UAF> ADD/IDENTIFIER MEMBERS_SUBSYSTEM- (1) _UAF> /ATTRIBUTES=(SUBSYSTEM,RESOURCE) UAF> GRANT/IDENTIFIER MEMBERS_SUBSYSTEM - (2) _UAF> /ATTRIBUTES=(SUBSYSTEM,RESOURCE) LOUIS UAF> GRANT/IDENTIFIER MEMBERS_SUBSYSTEM - _UAF> /ATTRIBUTES=(SUBSYSTEM,RESOURCE) WU $ SET SECURITY/ACL=(IDENTIFIER=MEMBERS_SUBSYSTEM,- (3) _$ ACCESS=CONTROL) MEMBER_LIST.EXE |
Note that you create the subsystem identifier MEMBERS_SUBSYSTEM with
the Resource attribute. This allows disk space to be charged to the
identifier MEMBERS_SUBSYSTEM and not the individuals accessing the
subsystem. (When using the Resource attribute, be careful to set the
appropriate ACLs on directories [see Section 8.8.1.2.3].)
13.6 Building the Subsystem
Once managers of the subsystem have the appropriate identifiers and access rights as described in Section 13.5, they can add the necessary ACEs to a subsystem image. Two kinds of ACEs are necessary to construct a subsystem: the application image receives a Subsystem ACE, and the objects managed by the subsystem receive Identifier ACEs. Therefore, building a subsystem requires the following steps:
|
(SUBSYSTEM,{IDENTIFIER=identifier[,ATTRIBUTES=attributes]}) |
|
(IDENTIFIER=identifier, ACCESS=access-type[+...]) |
In the following example, the subsystem manager uses the DCL command SET SECURITY to associate the subsystem identifier with the images that make up the subsystem. First, the subsystem manager adds a Subsystem ACE with the identifier MEMBERS_SUBSYSTEM to the ACL of the application image MEMBER_LIST.EXE:
$ SET SECURITY/ACL=(SUBSYSTEM,IDENTIFIER=MEMBERS_SUBSYSTEM,- _$ ATTRIBUTES=RESOURCE) MEMBER_LIST.EXE |
Then the subsystem manager adds an Identifier ACE with the subsystem identifier MEMBERS_SUBSYSTEM to the data files managed by the subsystem:
$ SET SECURITY/ACL=(IDENTIFIER=MEMBERS_SUBSYSTEM,- _$ ACCESS=READ+WRITE) MEMBER_DATA*.DAT |
The DCL command SHOW SECURITY displays the security attributes of the files. For example:
$ SHOW SECURITY MEMBER_LIST.EXE
MEMBER_LIST.EXE object of class FILE
Owner: [STAFF]
Protection: (System: RWED, Owner: RWED, Group, World: RE)
Access Control List: (SUBSYSTEM,IDENTIFIER=MEMBERS_SUBSYSTEM,ATTRIBUTES=RESOURCE)
|
$ SHOW SECURITY MEMBER_DATA*.DAT
MEMBER_DATA_1.DAT object of class FILE
Owner: MEMBERS_SUBSYSTEM
Protection: (System: RWED, Owner: RWED, Group, World)
Access Control List: (IDENTIFIER=MEMBERS_SUBSYSTEM,ACCESS=READ+WRITE)
MEMBER_DATA_2.DAT object of class FILE
Owner: MEMBERS_SUBSYSTEM
Protection: (System: RWED, Owner: RWED, Group, World)
Access Control List: (IDENTIFIER=MEMBERS_SUBSYSTEM, ACCESS=READ+WRITE)
|
A person with the SECURITY privilege can enable subsystems on a volume by using the /SUBSYSTEM qualifier on the MOUNT command. By default, subsystems are enabled only on the system disk. For other disks, you need to enable subsystems every time a volume is mounted.
In the following example, a security administrator uses the MOUNT command with the /SUBSYSTEM qualifier to enable the processing of Subsystem ACEs on device DUA0. Assume that this disk contains the subsystem with the identifier MEMBERS_SUBSYSTEM.
$ MOUNT /SUBSYSTEM /SYSTEM DUA0: DOC WORK8 |
You can turn the processing of Subsystem ACEs on and off dynamically with the DCL command SET VOLUME /SUBSYSTEM. This command is especially useful for the system disk, which is not mounted using the MOUNT command.
Any person mounting a subsystem is responsible for knowing what is on
the volume being mounted. Without this knowledge, an operator or system
manager can inadvertently subvert system security. For example, it is
easy for a user with privileges on one cluster to put an application
holding a subsystem identifier on a volume and then take the volume to
a naive operator on another cluster and request that it be mounted.
Because the application holds an appropriate subsystem identifier, it
feigns membership in a subsystem for which it is unauthorized.
Therefore, mount volumes of only those users whom you trust, or
thoroughly search a volume for Subsystem ACEs before you mount it with
subsystems enabled.
13.8 Giving Users Access
All users with execute access to the main application image of the subsystem can use the data files and other objects under control of the subsystem if the subsystem allows the access. However, managers of the subsystem can restrict access to objects of the subsystem in the following ways:
|
(ID=MEMBERS_SUBSYSTEM+MEMBERS_ADMIN, ACCESS=READ+WRITE) |
Remember that as long as users are executing the application image for
the subsystem, their process rights list contains the subsystem
identifier as well as their normal identifiers. However, as soon as
users interrupt or exit from the application, their process rights list
loses the subsystem identifier, and they lose access rights to the
objects in the subsystem. Subsystem identifiers are not propagated by
default when subprocesses are spawned.
13.9 Example of a Protected Subsystem
R. D. Taylor Inc., a company specializing in building supplies, decides to set up a protected subsystem for its purchasing and accounts payable departments. Although the departments are in different parts of the company, they share a common database for recording purchases from suppliers.
When the company's inventory drops below the desired level, the purchasing department is directed to order required supplies. Purchasing personnel find suppliers (if necessary), assign purchase order numbers, and issue a purchase orders.
When the goods arrive, the receiving and quality control departments check the contents against what was ordered, ensure the goods meet quality standards, and put the goods into inventory. Once the shipment is processed, the information goes to the accounts payable department, which settles the invoices.
Administrators in the accounts payable department check the invoices against purchase orders and run a payments program to calculate the monies due to suppliers each week. Payments are recorded in a database, and checks are printed on a printer loaded with company checks.
Using the subsystem lets the company meet two objectives:
The company appoints one employee, McGrey, to design and manage the subsystem. Figure 13-2 illustrates the directory structure of the Taylor subsystem, and Example 13-1 shows the command procedure McGrey wrote to implement it.
Figure 13-2 Directory Structure of the Taylor Company's Subsystem
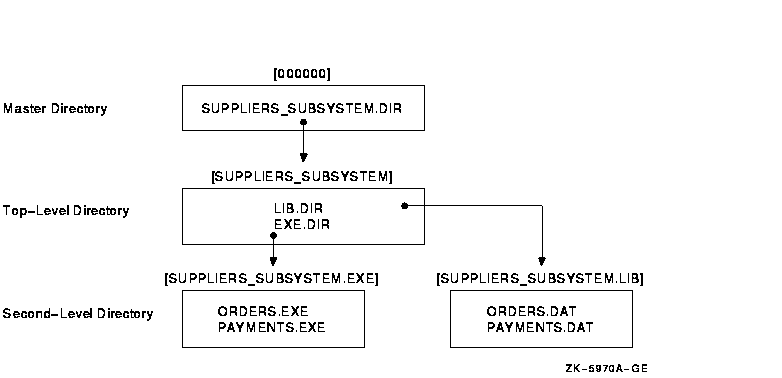
McGrey implements a directory structure in which users can gain access to the subsystem only by holding an appropriate identifier: purchasing personnel hold the identifier SUPPLIERS_ORDERS, and the accounts payable administrators hold the identifier ACCOUNTS_PAYABLE. As subsystem manager, McGrey holds the identifier SUPPLIERS_SUBSYSTEM.
The top-level directory SUPPLIERS_SUBSYSTEM.DIR has the following protection:
$ DIRECTORY/SECURITY SYS$SYSDEVICE:[000000]SUPPLIERS_SUBSYSTEM.DIR |
Directory SYS$SYSDEVICE:[000000]
SUPPLIERS_SUBSYSTEM.DIR;1
SUPPLIERS_SUBSYSTEM (RWE,RWE,,) (1)
(CREATOR,ACCESS=NONE) (2)
(DEFAULT_PROTECTION,SYSTEM:RWED,OWNER:RWED,GROUP:,WORLD:) (3)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL) (4)
(IDENTIFIER=SUPPLIERS_ORDERS,ACCESS=EXECUTE) (5)
(IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE) (6)
(IDENTIFIER=*,ACCESS=NONE) (7)
(IDENTIFIER=SUPPLIERS_SUBSYSTEM,OPTIONS=DEFAULT,ACCESS=READ+WRITE+CONTROL) (8)
(IDENTIFIER=SUPPLIERS_ORDERS,OPTIONS=DEFAULT,ACCESS=EXECUTE)
(IDENTIFIER=ACCOUNTS_PAYABLE,OPTIONS=DEFAULT,ACCESS=EXECUTE)
(IDENTIFIER=*,OPTIONS=DEFAULT,ACCESS=NONE)
Total of 1 file.
|
The directory EXE.DIR has the same protection as the top-level directory because subsystem users need to access the subsystem images: ORDERS.EXE and PAYMENTS.EXE. The other directory, LIB.DIR, is more restricted because only the subsystem images and McGrey need access.
$ DIRECTORY/SECURITY SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM...] |
Directory SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM] EXE.DIR;1 SUPPLIERS_SUBSYSTEM (RWE,RWE,,) (1) (CREATOR,ACCESS=NONE) (DEFAULT_PROTECTION,SYSTEM:RWED,OWNER:RWED,GROUP:,WORLD:) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL) (IDENTIFIER=SUPPLIERS_ORDERS,ACCESS=EXECUTE) (IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE) (IDENTIFIER=*,ACCESS=NONE) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,OPTIONS=DEFAULT,ACCESS=READ+WRITE+CONTROL) (IDENTIFIER=SUPPLIERS_ORDERS,OPTIONS=DEFAULT,ACCESS=EXECUTE) (IDENTIFIER=ACCOUNTS_PAYABLE,OPTIONS=DEFAULT,ACCESS=EXECUTE) (IDENTIFIER=*,OPTIONS=DEFAULT,ACCESS=NONE) LIB.DIR;1 SUPPLIERS_SUBSYSTEM (RWE,RWE,,) (2) (CREATOR,ACCESS=NONE) (DEFAULT_PROTECTION,SYSTEM:RWED,OWNER:RWED,GROUP:,WORLD:) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL) (IDENTIFIER=*,ACCESS=NONE) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,OPTIONS=DEFAULT,ACCESS=READ+WRITE+CONTROL) (IDENTIFIER=*,OPTIONS=DEFAULT,ACCESS=NONE) Total of 2 files. . . . |
As the following listing shows, the necessary company personnel can access the subsystem's images, ORDERS.EXE and PAYMENTS.EXE, but only the images can update the data files:
Directory SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM.EXE] ORDERS.EXE;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,) (1) (SUBSYSTEM,IDENTIFIER=SUPPLIERS_SUBSYSTEM,ATTRIBUTES=RESOURCE) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL) (IDENTIFIER=SUPPLIERS_ORDERS,ACCESS=EXECUTE) (IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE) (IDENTIFIER=*,ACCESS=NONE) PAYMENTS.EXE;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,) (2) (SUBSYSTEM,IDENTIFIER=SUPPLIERS_SUBSYSTEM,ATTRIBUTES=RESOURCE) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE+CONTROL) (IDENTIFIER=ACCOUNTS_PAYABLE,ACCESS=EXECUTE) (IDENTIFIER=*,ACCESS=NONE) Total of 2 files. Directory SYS$SYSDEVICE:[SUPPLIERS_SUBSYSTEM.LIB] (3) ORDERS.DAT;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE) (IDENTIFIER=*,ACCESS=NONE) PAYMENTS.DAT;1 SUPPLIERS_SUBSYSTEM (RWED,RWED,,) (IDENTIFIER=SUPPLIERS_SUBSYSTEM,ACCESS=READ+WRITE) (IDENTIFIER=*,ACCESS=NONE) Total of 2 files. Grand total of 3 directories, 6 files. |
| Previous | Next | Contents | Index |