 |
HP OpenVMS System Services Reference Manual
$AUDIT_EVENT
Appends an event message to the system security audit log file or sends
an alarm to a security operator terminal.
Format
SYS$AUDIT_EVENT [efn] ,[flags] ,itmlst ,[audsts] ,[astadr] ,[astprm]
C Prototype
int sys$audit_event (unsigned int efn, unsigned int flags, void
*itmlst, unsigned int *audsts, void (*astadr)(__unknown_params), int
astprm);
Arguments
efn
| OpenVMS usage: |
ef_number |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Number of the event flag to be set when the audit completes. The
efn argument is a longword containing the number of
the event flag; however, $AUDIT_EVENT uses only the low-order byte. If
efn is not specified, event flag 0 is used.
Upon request initiation, $AUDIT_EVENT clears the specified event flag.
flags
| OpenVMS usage: |
mask_longword |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Flags specifying options for the $AUDIT_EVENT system operation. The
flags argument is a longword bit mask, where each bit
corresponds to an option.
Each flag option has a symbolic name. The $NSADEF macro defines the
following symbolic names:
| Symbolic Name |
Description |
|
NSA$M_ACL
|
Specifies an event generated by an Alarm ACE or Audit ACE. This flag is
reserved to HP.
|
|
NSA$M_FLUSH
|
Specifies that all messages in the audit server buffer be written to
the audit log file.
|
|
NSA$M_INTERNAL
|
Specifies that the $AUDIT_EVENT call originates in the context of a
trusted computing base (TCB) component. The auditing components use
this flag to indicate that internal auditing failures should result in
a SECAUDTCB bugcheck. This flag is reserved to HP.
|
|
NSA$M_MANDATORY
|
Specifies that an audit is to be performed, regardless of system alarm
and audit settings.
|
|
NSA$M_NOEVTCHECK
|
Specifies that an audit is to be performed, regardless of the system
alarm or audit settings. This flag is similar to the NSA$M_MANDATORY
bit but, unlike the NSA$M_MANDATORY bit, this flag is not reflected in
the NSA$W_FLAGS field in the resulting audit record on disk.
|
|
NSA$M_SERVER
|
Indicates that the call originates in a TCB server process and that the
event should be audited regardless of the state of a process-specific,
no-audit bit.
Trusted servers use this flag to override the no-audit bit when
they want to perform explicit auditing on behalf of a client process.
This flag is reserved to HP.
|
itmlst
| OpenVMS usage: |
item_list_3 |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by reference |
Item list specifying information to include in the audit record. The
itmlst argument is the address of a list of item
descriptors. The list of item descriptors is terminated by a longword
of 0.
The item list for all calls to $AUDIT_EVENT must include the following
item codes:
- NSA$_EVENT_TYPE (see Table SYS-17)
- NSA$_EVENT_SUBTYPE (see Table SYS-17)
- At least one of the NSA$_ALARM_NAME item code or the
NSA$_AUDIT_NAME item code.
- If the event being reported is an object access
(NSA$C_MSG_OBJ_ACCESS) or an object delete (NSA$C_MSG_OBJ_DELETE), the
NSA$_FINAL_STATUS, NSA$_ACCESS_DESIRED, and NSA$_OBJECT_CLASS item
codes must be specified.
- If the event being reported is an object create
(NSA$C_MSG_OBJ_CREATE), the NSA$_FINAL_STATUS and NSA$_OBJECT_CLASS
item codes must be specified.
- If the event being reported is a privilege audit
(NSA$C_MSG_PRVAUD), the NSA$_PRIVS_USED or the NSA$_PRIVS_MISSING item
code must be specified.
- If the audit event being reported is a deaccess event
(NSA$C_MSG_OBJ_DEACCESS), the NSA$_OBJECT_CLASS item code must be
specified.
The item list is a standard format item list. The following diagram
depicts the general structure of an item descriptor:
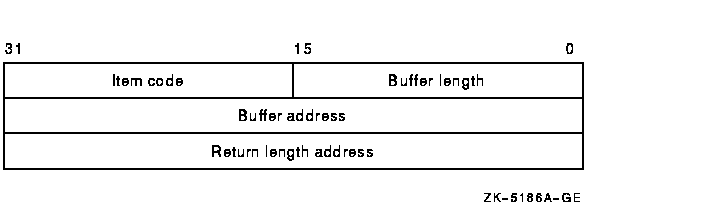
The following table defines the item descriptor fields:
| Descriptor Field |
Definition |
|
Buffer length
|
A word specifying the length (in bytes) of the buffer; the buffer
supplies information to be used by $AUDIT_EVENT. The required length of
the buffer varies, depending on the item code specified; each item code
description specifies the required length.
|
|
Item code
|
A word containing a symbolic code describing the nature of the
information currently in the buffer. The location of the buffer is
pointed to by the buffer address field. Each item code has a symbolic
name. This section provides a detailed description of item codes
following the description of arguments.
|
|
Buffer address
|
A longword containing the address of the buffer that specifies the
information.
|
|
Return length address
|
Not currently used; this field is reserved to HP. You must specify 0.
|
See the Item Codes section for a description of the $AUDIT_EVENT item
codes.
audsts
| OpenVMS usage: |
cond_value_type |
| type: |
longword (unsigned) |
| access: |
write only |
| mechanism: |
by reference |
Longword condition value that receives the final completion status from
the operation. If a security audit is required, the final completion
status represents either the successful completion of the resulting
security audit or any failing status that occurred while the security
audit was performed within the audit server process.
The audsts argument is valid only when the service
returns success and the status is not SS$_EVTNOTENAB. In addition, the
caller must either make use of the astadr argument or
use the $AUDIT_EVENTW service before attempting to access
audsts.
astadr
| OpenVMS usage: |
ast_procedure |
| type: |
procedure value |
| access: |
call without stack unwinding |
| mechanism: |
by reference |
Asynchronous system trap (AST) routine to be executed after the
audsts is updated. The astadr
argument, which is the address of a longword value, is the procedure
value of the AST routine.
The AST routine executes in the access mode of the caller of
$AUDIT_EVENT.
astprm
| OpenVMS usage: |
user_arg |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Asynchronous system trap (AST) parameter passed to the AST service
routine. The astprm argument is a longword value
containing the AST parameter.
Item Codes
This section provides a list of item codes that can be used to affect
auditing.
NSA$_ALARM_NAME
NSA$_ALARM_NAME is a string of 1 to 32 characters specifying an alarm
journal name to receive the record. To direct an event to the system
alarm journal (that is, all enabled security operator terminals), use
the string SECURITY.
NSA$_AUDIT_NAME
NSA$_AUDIT_NAME is a string of 1 to 65 characters specifying the
journal file to receive the audit record. To direct an event to the
system audit journal, use the string SECURITY.
NSA$_CHAIN
NSA$_CHAIN is a longword value specifying the item list to process
immediately after the current one. The buffer address field in the item
descriptor specifies the address of the next item list to be processed.
Anything after NSA$_CHAIN is ignored.
NSA$_EVENT_FACILITY
NSA$_EVENT_FACILITY is a word value specifying the facility generating
the event. All operating system events are audited as facility zero.
NSA$_EVENT_SUBTYPE
NSA$_EVENT_SUBTYPE is a longword value specifying an event message
subtype. See Table SYS-17 for a list of valid event subtypes.
NSA$_EVENT_TYPE
NSA$_EVENT_TYPE is a longword value specifying an event message type.
See Table SYS-17 for a list of valid event types.
Table SYS-17 Description of$AUDIT_EVENT Types and Subtypes
| Symbol of Event Type |
Meaning |
|
NSA$C_MSG_AUDIT
|
Systemwide change to auditing
|
Subtype and Meaning
NSA$C_AUDIT_DISABLED
NSA$C_AUDIT_ENABLED
NSA$C_AUDIT_INITIATE
NSA$C_AUDIT_TERMINATE
NSA$C_AUDIT_LOG_FINAL
NSA$C_AUDIT_LOG_FIRST
|
Audit events disabled
Audit events enabled
Audit server startup
Audit server shutdown
Final entry in audit log (forward link)
First entry in audit log (backward link)
|
|
|
|
|
NSA$C_MSG_BREAKIN
|
Break-in attempt detected
|
Subtype and Meaning
NSA$C_DETACHED
NSA$C_DIALUP
NSA$C_LOCAL
NSA$C_NETWORK
NSA$C_REMOTE
|
Detached process
Dialup interactive process
Local interactive process
Network server process
Interactive process from another network node
|
|
|
|
|
NSA$C_MSG_CONNECTION
|
Logical link connection or termination
|
Subtype and Meaning
NSA$C_CNX_ABORT
NSA$C_CNX_ACCEPT
NSA$C_CNX_DECNET_CREATE
NSA$C_CNX_DECNET_DELETE
NSA$C_CNX_DISCONNECT
NSA$C_CNX_IPC_CLOSE
NSA$C_CNX_IPC_OPEN
NSA$C_CNX_REJECT
NSA$C_CNX_REQUEST
NSA$C_CNX_INC_REQUEST
NSA$C_CNX_INC_ACCEPT
NSA$C_CNX_INC_REJECT
NSA$C_CNX_INC_DISCONNECT
NSA$C_CNX_INC_ABORT
|
Connection aborted
Connection accepted
DECnet for OpenVMS logical link created
DECnet for OpenVMS logical link disconnected
Connection disconnected
Interprocess communication association closed
Interprocess communication association opened
Connection rejected
Connection requested
Incoming connection requested
Incoming connection accepted
Incoming connection rejected
Incoming connection disconnected
Incoming connection aborted
|
|
|
|
|
NSA$C_MSG_INSTALL
|
Use of the Install utility (INSTALL)
|
Subtype and Meaning
NSA$C_INSTALL_ADD
NSA$C_INSTALL_REMOVE
|
Known image installed
Known image deleted
|
|
|
|
|
NSA$C_MSG_LOGFAIL
|
Login failure
|
Subtype and Meaning
NSA$C_BATCH
NSA$C_DETACHED
NSA$C_DIALUP
NSA$C_LOCAL
NSA$C_NETWORK
NSA$C_REMOTE
NSA$C_SUBPROCESS
|
Batch process
Detached process
Dialup interactive process
Local interactive process
Network server process
Interactive process from another network node
Subprocess
|
|
|
|
|
NSA$C_MSG_LOGIN
|
Successful login
|
Subtype and Meaning
See subtypes for NSA$C_MSG_
LOGFAIL
|
|
|
|
|
|
NSA$C_MSG_LOGOUT
|
Successful logout
|
Subtype and Meaning
See subtypes for NSA$C_MSG_
LOGFAIL
|
|
|
|
|
|
NSA$C_MSG_MOUNT
|
Volume mount or dismount
|
Subtype and Meaning
NSA$C_VOL_DISMOUNT
NSA$C_VOL_MOUNT
|
Volume dismount
Volume mount
|
|
|
|
|
NSA$C_MSG_NCP
|
Modification to network configuration database
|
Subtype and Meaning
NSA$C_NCP_COMMAND
|
Network Control Program (NCP) command issued
|
|
|
|
|
NSA$C_MSG_NETPROXY
|
Modification to network proxy database
|
Subtype and Meaning
NSA$C_NETPROXY_ADD
NSA$C_NETPROXY_DELETE
NSA$C_NETPROXY_MODIFY
|
Record added to network proxy database
Record removed from network proxy database
Record modified in network proxy database
|
|
|
|
|
NSA$C_MSG_OBJ_ACCESS
|
Object access attempted
|
Subtype and Meaning
NSA$C_OBJ_ACCESS
|
Object access attempted
|
|
|
|
|
NSA$C_MSG_OBJ_CREATE
|
Object created
|
Subtype and Meaning
NSA$C_OBJ_CREATE
|
Object created
|
|
|
|
|
NSA$C_MSG_OBJ_DEACCESS
|
Object deaccessed
|
Subtype and Meaning
NSA$C_OBJ_DEACCESS
|
Object deaccessed
|
|
|
|
|
NSA$C_MSG_OBJ_DELETE
|
Object deleted
|
Subtype and Meaning
NSA$C_OBJ_DELETE
|
Object deleted
|
|
|
|
|
NSA$C_MSG_PROCESS
|
Process control system service issued
|
Subtype and Meaning
NSA$C_PRC_CANWAK
NSA$C_PRC_CREPRC
NSA$C_PRC_DELPRC
NSA$C_PRC_FORCEX
NSA$C_PRC_GETJPI
NSA$C_PRC_GRANTID
NSA$C_PRC_RESUME
NSA$C_PRC_REVOKID
NSA$C_PRC_SCHDWK
NSA$C_PRC_SETPRI
NSA$C_PRC_SIGPRC
NSA$C_PRC_SUSPND
NSA$C_PRC_WAKE
NSA$C_PRC_PRCTERM
|
Process wakeup canceled
Process created
Process deleted
Process exit forced
Process information gathered
Process identifier granted
Process resumed
Process identifier revoked
Process wakeup scheduled
Process priority altered
Process exception issued
Process suspended
Process wakeup issued
Process termination notification requested
|
|
|
|
|
NSA$C_MSG_PRVAUD
|
Attempt to use privilege
|
Subtype and Meaning
NSA$C_PRVAUD_FAILURE
NSA$C_PRVAUD_SUCCESS
|
Unsuccessful use of privilege
Successful use of privilege
|
|
|
|
|
NSA$C_MSG_RIGHTSDB
|
Modification to rights database
|
Subtype and Meaning
NSA$C_RDB_ADD_ID
NSA$C_RDB_CREATE
NSA$C_RDB_GRANT_ID
NSA$C_RDB_MOD_HOLDER
NSA$C_RDB_MOD_ID
NSA$C_RDB_REM_ID
NSA$C_RDB_REVOKE_ID
|
Identifier added to rights database
Rights database created
Identifier given to user
List of identifier holders modified
Identifier name or attributes modified
Identifier removed from rights database
Identifier revoked from user
|
|
|
|
|
NSA$C_MSG_SYSGEN
|
Modification of a system parameter using the System Generation utility
(SYSGEN)
|
Subtype and Meaning
NSA$C_SYSGEN_SET
|
System parameter modified
|
|
|
|
|
NSA$C_MSG_SYSTIME
|
Modification to system time
|
Subtype and Meaning
NSA$C_SYSTIM_SET
NSA$C_SYSTIM_CAL
|
System time set
System time calibrated
|
|
|
|
|
NSA$C_MSG_SYSUAF
|
Modification to system user authorization file (SYSUAF)
|
Subtype and Meaning
NSA$C_SYSUAF_ADD
NSA$C_SYSUAF_COPY
NSA$C_SYSUAF_DELETE
NSA$C_SYSUAF_MODIFY
NSA$C_SYSUAF_RENAME
|
Record added to SYSUAF
Record copied in SYSUAF
Record deleted from SYSUAF
Record modified in SYSUAF
Record renamed in SYSUAF
|
NSA$_FIELD_NAME
NSA$_FIELD_NAME is a string of 1 to 256 characters specifying the name
of the field being modified. This is used in combination with
NSA$_ORIGINAL_DATA and NSA$_NEW_DATA.
NSA$_MESSAGE
NSA$_MESSAGE specifies a system message code. The $FORMAT_AUDIT service
will use the $GETMSG service to translate the message into text. The
resulting text is inserted into the formatted audit message, with the
"Event information:" prefix. For example, the operating
system uses this item code to supply the privilege audit text
associated with privilege audit events; this keeps the audit records
small. By default, the $GETMSG service can only translate resident
system messages. You can use the NSA$_MSGFILNAM item code to specify
the name of an application or site-specific message file.
NSA$_MSGFILNAM
NSA$_MSGFILNAM is a string of 1 to 255 characters specifying the
message file containing the translation for the message code in
NSA$_MESSAGE. The default file specification is SYS$MESSAGE:.EXE. By
default, $FORMAT_AUDIT uses the resident system message file.
NSA$_NEW_DATA
NSA$_NEW_DATA is a string of 1 to n characters specifying the
contents of the field named in NSA$_FIELD_NAME after the event
occurred. NSA$_ORIGINAL_DATA contains the field contents prior to the
event.
NSA$_NOP
NSA$_NOP specifies that the item list entry should be ignored. This
item code allows you to build a static item list and then remove those
entries that do not apply to the current event.
NSA$_ORIGINAL_DATA
NSA$_ORIGINAL_DATA is a string of 1 to n characters specifying
the contents of the field named in NSA$_FIELD_NAME before the event
occurred. NSA$_NEW_DATA contains the field contents following the event.
NSA$_SENSITIVE_FIELD_NAME
NSA$_SENSITIVE_FIELD_NAME is a string of 1 to 256 characters specifying
the name of the field being modified. This is used in combination with
NSA$_SENSITIVE_ORIG_DATA and NSA$_SENSITIVE_NEW_DATA. Use
NSA$_SENSITIVE_FIELD_NAME to prevent sensitive information, such as
passwords, from being displayed in an alarm message. Sensitive
information is written to the audit log.
NSA$_SENSITIVE_NEW_DATA
NSA$_SENSITIVE_NEW_DATA is a string of 1 to n characters
specifying the contents of the field named in NSA$_SENSITIVE_FIELD_NAME
after the event occurred. NSA$_SENSITIVE_ORIG_DATA contains the field
contents prior to the event. Use NSA$_SENSITIVE_NEW_DATA to prevent
sensitive information from being displayed in an alarm message.
Sensitive information is written to the audit log.
NSA$_SENSITIVE_ORIG_DATA
NSA$_SENSITIVE_ORIG_DATA is a string of 1 to n characters
specifying the contents of the field named in NSA$_SENSITIVE_FIELD_NAME
before the event occurred. NSA$_SENSITIVE_NEW_DATA contains the field
contents following the event. Use NSA$_SENSITIVE_FIELD_NAME to prevent
sensitive information from being displayed in an alarm message.
Sensitive information is written to the audit log.
NSA$_SUPPRESS
NSA$_SUPPRESS is a longword bit mask directing $AUDIT_EVENT to ignore
the defaults for the following values and either omit the information
from the event record or use the value provided in another parameter.
The bits in the mask inhibit the use of default values for the
following item codes:
|
NSA$V_ACCOUNT_NAME
|
NAS$V_PROCESS_NAME
|
|
NSA$V_FINAL_STATUS
|
NSA$V_SUBJECT_CLASS
|
|
NSA$V_IMAGE_NAME
|
NSA$V_SUBJECT_OWNER
|
|
NSA$V_PARENT_ID
|
NSA$V_SYSTEM_ID
|
|
NSA$V_PARENT_NAME
|
NSA$V_SYSTEM_OWNER
|
|
NSA$V_PARENT_OWNER
|
NSA$V_TERMINAL
|
|
NSA$V_PARENT_USERNAME
|
NSA$V_TIME_STAMP
|
|
NSA$V_PROCESS_ID
|
NSA$V_USERNAME
|
Use NSA$_SUPPRESS, for example, when auditing events from server
processes when the default values for many of these items need to
explicitly reference the client context rather than be defaulted from
the environment of the server.
The following section provides a list of additional item codes that are
valid as an item descriptor in the itmlst argument.
NSA$_ACCESS_DESIRED
NSA$_ACCESS_DESIRED is a longword value specifying the access request
mask as defined in $ARMDEF.
NSA$_ACCESS_MODE
NSA$_ACCESS_MODE is a byte value specifying an access mode associated
with the event.
NSA$_ACCOUNT
NSA$_ACCOUNT is a string of 1 to 32 characters specifying the account
name associated with the event.
NSA$_ASSOCIATION_NAME
NSA$_ASSOCIATION_NAME is a string of 1 to 256 characters specifying an
association name.
NSA$_COMMAND_LINE
NSA$_COMMAND_LINE is a string of 1 to 2048 characters specifying a
command line.
NSA$_CONNECTION_ID
NSA$_CONNECTION_ID is a longword value specifying a connection
identification.
NSA$_DECNET_LINK_ID
NSA$_DECNET_LINK_ID is a longword value specifying a DECnet for OpenVMS
logical link identification.
NSA$_DECNET_OBJECT_NAME
NSA$_DECNET_OBJECT_NAME is a string of 1 to 16 characters specifying a
DECnet for OpenVMS object name.
NSA$_DECNET_OBJECT_NUMBER
NSA$_DECNET_OBJECT_NUMBER is a longword value specifying a DECnet for
OpenVMS object number.
NSA$_DEFAULT_USERNAME
NSA$_DEFAULT_USERNAME is a string of 1 to 32 characters specifying a
default local user name for incoming network proxy requests.
NSA$_DEVICE_NAME
NSA$_DEVICE_NAME is a string of 1 to 64 characters specifying the name
of the device where the volume resides.
NSA$_DIRECTORY_ENTRY
NSA$_DIRECTORY_ENTRY is a string of 1 to 256 characters specifying the
name of the directory entry associated with an XQP operation.
NSA$_DIRECTORY_ID
NSA$_DIRECTORY_ID is an array of three words specifying the directory
file identification.
NSA$_DISMOUNT_FLAGS
NSA$_DISMOUNT_FLAGS is a longword value specifying the dismount flags
that are defined by the $DMTDEF macro in STARLET.
NSA$_EFC_NAME
NSA$_EFC_NAME is a string of 1 to 16 characters specifying the event
flag cluster name.
NSA$_FILE_ID
NSA$_FILE_ID is an array of three words specifying the file
identification.
NSA$_FINAL_STATUS
NSA$_FINAL_STATUS is a longword value specifying the successful or
unsuccessful status that caused the auditing facility to be invoked.
NSA$_HOLDER_NAME
NSA$_HOLDER_NAME is a string of 1 to 32 characters specifying the name
of the user holding the identifier.
NSA$_HOLDER_OWNER
NSA$_HOLDER_OWNER is a longword value specifying the owner (UIC) of the
holder.
NSA$_ID_ATTRIBUTES
NSA$_ID_ATTRIBUTES is a longword value specifying the attributes of the
identifier, which are defined by the $KGBDEF macro in STARLET.
NSA$_IDENTIFIERS_USED
NSA$_IDENTIFIERS_USED is an array of longwords specifying the
identifiers (from the access control entry [ACE] granting access) that
were used to gain access to the object.
NSA$_ID_NAME
NSA$_ID_NAME is a string of 1 to 32 characters specifying the name of
the identifier.
NSA$_ID_NEW_ATTRIBUTES
NSA$_ID_NEW_ATTRIBUTES is a longword value specifying the new
attributes of the identifier, which are defined by the $KGBDEF macro in
STARLET.
NSA$_ID_NEW_NAME
NSA$_ID_NEW_NAME is a string of 1 to 32 characters specifying the new
name of the identifier.
NSA$_ID_NEW_VALUE
NSA$_ID_NEW_VALUE is a longword value specifying the new value of the
identifier.
NSA$_ID_VALUE
NSA$_ID_VALUE is a longword value specifying the value of the
identifier.
NSA$_ID_VALUE_ASCII
NSA$_ID_VALUE_ASCII is a longword specifying the value of the
identifier.
NSA$_IMAGE_NAME
NSA$_IMAGE_NAME is a string of 1 to 1024 characters specifying the name
of the image being executed when the event took place.
NSA$_INSTALL_FILE
NSA$_INSTALL_FILE is a string of 1 to 255 characters specifying the
name of the installed file.
NSA$_INSTALL_FLAGS
NSA$_INSTALL_FLAGS is a longword value specifying the INSTALL flags.
They correspond to qualifiers for the Install utility; for example,
NSA$M_INS_EXECUTE_ONLY.
NSA$_LNM_PARENT_NAME
NSA$_LNM_PARENT_NAME is a string of 1 to 31 characters specifying the
name of the parent logical name table.
NSA$_LNM_TABLE_NAME
NSA$_LNM_TABLE_NAME is a string of 1 to 31 characters specifying the
name of the logical name table.
NSA$_LOCAL_USERNAME
NSA$_LOCAL_USERNAME is a string of 1 to 32 characters specifying user
names of the accounts available for incoming network proxy requests.
NSA$_LOGICAL_NAME
NSA$_LOGICAL_NAME is a string of 1 to 255 characters specifying the
logical name associated with the device.
NSA$_MAILBOX_UNIT
NSA$_MAILBOX_UNIT is a longword value specifying the mailbox unit
number.
NSA$_MATCHING_ACE
NSA$_MATCHING_ACE is an array of bytes specifying the ACE granting or
denying access.
NSA$_MOUNT_FLAGS
NSA$_MOUNT_FLAGS is a quadword value specifying mount flags that are
defined by the $MNTDEF macro in STARLET.
NSA$_NEW_IMAGE_NAME
NSA$_NEW_IMAGE_NAME is a string of 1 to 1024 characters specifying the
name of the new image.
NSA$_NEW_OWNER
NSA$_NEW_OWNER is a longword value specifying the new process owner
(UIC).
NSA$_NEW_PRIORITY
NSA$_NEW_PRIORITY is a longword value specifying the new process
priority.
NSA$_NEW_PRIVILEGES
NSA$_NEW_PRIVILEGES is a quadword privilege mask specifying the new
privileges. The $PRVDEF macro defines the list of available privileges.
NSA$_NEW_PROCESS_ID
NSA$_NEW_PROCESS_ID is a longword value specifying the new process
identification.
NSA$_NEW_PROCESS_NAME
NSA$_NEW_PROCESS_NAME is a string of 1 to 15 characters specifying the
name of the new process.
NSA$_NEW_PROCESS_OWNER
NSA$_NEW_PROCESS_OWNER is a longword value specifying the owner (UIC)
of the new process.
NSA$_NEW_USERNAME
NSA$_NEW_USERNAME is a string of 1 to 32 characters specifying the new
user name.
NSA$_OBJECT_CLASS
NSA$_OBJECT_CLASS is a string of 1 to 23 characters specifying the
security object class associated with the event; for example, FILE.
NSA$_OBJECT_ID
NSA$_OBJECT_ID is an array of three words specifying the unique object
identification code, which is currently applicable only to files;
therefore, it is the file identification.
NSA$_OBJECT_MAX_CLASS
NSA$_OBJECT_MAX_CLASS is a 20-byte record specifying the maximum access
classification of the object.
NSA$_OBJECT_MIN_CLASS
NSA$_OBJECT_MIN_CLASS is a 20-byte record specifying the minimum access
classification of the object.
NSA$_OBJECT_NAME
NSA$_OBJECT_NAME is a string of 1 to 255 characters specifying an
object's name.
NSA$_OBJECT_NAME_2
NSA$_OBJECT_NAME_2 is a string of 1 to 255 characters specifying an
alternate object name; currently it applies to file-backed global
sections where the alternate name of a global section is the file name.
NSA$_OBJECT_OWNER
NSA$_OBJECT_OWNER is a longword value specifying the UIC or general
identifier of the process causing the auditable event.
NSA$_OBJECT_PROTECTION
NSA$_OBJECT_PROTECTION is a word, or an array of four longwords,
specifying the UIC-based protection of the object.
NSA$_OLD_PRIORITY
NSA$_OLD_PRIORITY is a longword value specifying the former process
priority.
NSA$_OLD_PRIVILEGES
NSA$_OLD_PRIVILEGES is a quadword privilege mask specifying the former
privileges. The $PRVDEF macro defines the list of available privileges.
NSA$_PARAMS_INUSE
NSA$_PARAMS_INUSE is a string of 1 to 255 characters specifying the
name of the parameter file given to the SYSGEN command USE.
NSA$_PARAMS_WRITE
NSA$_PARAMS_WRITE is a string of 1 to 255 characters specifying the
file name for the SYSGEN command WRITE.
NSA$_PARENT_ID
NSA$_PARENT_ID is a longword value specifying the process
identification (PID) of the parent process. It is used only when
auditing events pertaining to a subprocess.
NSA$_PARENT_NAME
NSA$_PARENT_NAME is a string of 1 to 15 characters specifying the
parent's process name. It is used only when auditing events pertaining
to a subprocess.
NSA$_PARENT_OWNER
NSA$_PARENT_OWNER is longword value specifying the owner (UIC) of the
parent process. It is used only when auditing events pertaining to a
subprocess.
NSA$_PARENT_USERNAME
NSA$_PARENT_USERNAME is a string of 1 to 32 characters specifying the
user name associated with the parent process. It is used only when
auditing events pertaining to a subprocess.
NSA$_PASSWORD
NSA$_PASSWORD is a string of 1 to 32 characters specifying the password
used in an unsuccessful break-in attempt. By default, system security
alarms do not include break-in passwords.
NSA$_PRIVILEGES
NSA$_PRIVILEGES is a quadword privilege mask specifying the privileges
used to gain access. The $PRVDEF macro defines the list of available
privileges.
NSA$_PRIVS_MISSING
NSA$_PRIVS_MISSING is a longword or a quadword privilege mask
specifying the privileges that are needed. The privileges are defined
by a macro in STARLET; see the $CHPDEF macro for definition as a
longword mask, and see the $PRVDEF macro for definition as a quadword
privilege mask.
NSA$_PRIVS_USED
NSA$_PRIVS_USED is a longword or a quadword privilege mask specifying
the privileges used to gain access to the object. The privileges are
defined by a macro in STARLET; see the $CHPDEF macro for definition as
a longword mask and see the $PRVDEF macro for definition as a quadword
privilege mask.
NSA$_PROCESS_ID
NSA$_PROCESS_ID is a longword value specifying the PID of the process
causing the auditable event.
NSA$_PROCESS_NAME
NSA$_PROCESS_NAME is a string of 1 to 15 characters specifying the
process name that caused the auditable event.
NSA$_REM_ASSOCIATION_NAME
NSA$_REM_ASSOCIATION_NAME is a string of 1 to 256 characters specifying
the interprocess communication (IPC) remote association name.
NSA$_REMOTE_LINK_ID
NSA$_REMOTE_LINK_ID is a longword value specifying the remote logical
link ID.
NSA$_REMOTE_NODE_FULLNAME
NSA$_REMOTE_NODE_FULLNAME is a string of 1 to 255 characters specifying
the fully expanded DECnet for OpenVMS node name of the remote process.
NSA$_REMOTE_NODE_ID
NSA$_REMOTE_NODE_ID is a string of 4 to 24 characters specifying the
DECnet for OpenVMS node address of the remote process. A value 4 bytes
in length is a DECnet Phase IV node address. A value with length
greater than 4 bytes is a DECnet/OSI NSAP address.
NSA$_REMOTE_NODENAME
NSA$_REMOTE_NODENAME is a string of 1 to 6 characters specifying the
DECnet for OpenVMS node name of the remote process.
NSA$_REMOTE_USERNAME
NSA$_REMOTE_USERNAME is a string of 1 to 32 characters specifying the
user name of the remote process.
NSA$_REQUEST_NUMBER
NSA$_REQUEST_NUMBER is a longword value specifying the request number
associated with the system service call.
NSA$_RESOURCE_NAME
NSA$_RESOURCE_NAME is a string of 1 to 32 characters specifying the
lock resource name.
NSA$_SECTION_NAME
NSA$_SECTION_NAME is a string of 1 to 42 characters specifying the
global section name.
NSA$_SNAPSHOT_BOOTFILE
NSA$_SNAPSHOT_BOOTFILE is a string of 1 to 255 characters specifying
the name of the snapshot boot file, the saved system image file from
which the system just booted.
NSA$_SNAPSHOT_SAVE_FILNAM
NSA$_SNAPSHOT_SAVE_FILNAM is a string of 1 to 255 characters specifying
the name of the snapshot save file, which is the original location of
the snapshot file at the time that the system was saved.
NSA$_SNAPSHOT_TIME
NSA$_SNAPSHOT_TIME is a quadword value specifying the time the picture
of the configuration was taken and saved in the snapshot boot file.
NSA$_SOURCE_PROCESS_ID
NSA$_SOURCE_PROCESS_ID is a longword value specifying the process
identification of the process originating the request.
NSA$_SUBJECT_CLASS
NSA$_SUBJECT_CLASS is a 20-byte record specifying the current access
class of the process causing the auditable event.
NSA$_SUBJECT_OWNER
NSA$_SUBJECT_OWNER is a longword value specifying the owner (UIC) of
the process causing the event.
NSA$_SYSTEM_ID
NSA$_SYSTEM_ID is a longword value specifying the SCS identification of
the cluster node where the event took place (system parameter
SCSSYSTEMID).
NSA$_SYSTEM_NAME
NSA$_SYSTEM_NAME is a string of 1 to 6 characters specifying the System
Communications Services (SCS) node name where the event took place
(system parameter SCSNODE).
NSA$_SYSTEM_SERVICE_NAME
NSA$_SYSTEM_SERVICE_NAME is a string of 1 to 256 characters specifying
the name of the system service associated with the event.
NSA$_SYSTIM_NEW
NSA$_SYSTIM_NEW is a quadword value specifying the new system time.
NSA$_SYSTIM_OLD
NSA$_SYSTIM_OLD is a quadword value specifying the old system time.
NSA$_TARGET_DEVICE_NAME
NSA$_TARGET_DEVICE_NAME is a string of 1 to 64 characters specifying
the target device name.
NSA$_TARGET_PROCESS_CLASS
NSA$_TARGET_PROCESS_CLASS is a 20-byte record specifying the target
process classification.
NSA$_TARGET_PROCESS_ID
NSA$_TARGET_PROCESS_ID is a longword value specifying the target
process identifier (PID).
NSA$_TARGET_PROCESS_NAME
NSA$_TARGET_PROCESS_NAME is a string of 1 to 64 characters specifying
the target process name.
NSA$_TARGET_PROCESS_OWNER
NSA$_TARGET_PROCESS_OWNER is a longword value specifying the target
owner (UIC).
NSA$_TARGET_USERNAME
NSA$_TARGET_USERNAME is a string of 1 to 32 characters specifying the
target process user name.
NSA$_TERMINAL
NSA$_TERMINAL is a string of 1 to 256 characters specifying the name of
the terminal to which the process was connected when the auditable
event occurred.
NSA$_TIME_STAMP
NSA$_TIME_STAMP is a quadword value specifying the time when the event
occurred.
NSA$_TRANSPORT_NAME
NSA$_TRANSPORT_NAME is a string of 1 to 256 characters specifying the
name of the transport: interprocess communication, DECnet for OpenVMS,
or System Management Integrator (SMI), which handles requests from
SYSMAN (ASCII string).
NSA$_UAF_ADD
NSA$_UAF_ADD is a string of 1 to 32 characters specifying the name of
the authorization record being added.
NSA$_UAF_COPY
NSA$_UAF_COPY is a string of 1 to 32 characters specifying the new name
of the authorization record being copied from NSA$_UAF_SOURCE.
NSA$_UAF_DELETE
NSA$_UAF_DELETE is a string of 1 to 32 characters specifying the name
of the authorization record being removed.
NSA$_UAF_MODIFY
NSA$_UAF_MODIFY is a string of 1 to 32 characters specifying the name
of the authorization record being modified.
NSA$_UAF_RENAME
NSA$_UAF_RENAME is a string of 1 to 32 characters specifying the name
of the authorization record being renamed.
NSA$_UAF_SOURCE
NSA$_UAF_SOURCE is a string of 1 to 32 characters specifying the user
name of the source record for an Authorize utility (AUTHORIZE) copy
operation.
NSA$_USERNAME
NSA$_USERNAME is a string of 1 to 32 characters specifying the user
name of the process causing the auditable event.
NSA$_VOLUME_NAME
NSA$_VOLUME_NAME is a string of 1 to 15 characters specifying a volume
name.
NSA$_VOLUME_SET_NAME
NSA$_VOLUME_SET_NAME is a string of 1 to 15 characters specifying a
volume set name.
Description
The Audit Event service can be called by any program that enforces a
security policy to append an event message to the audit log file or
send an alarm to an operator terminal. For example, AUTHORIZE calls
$AUDIT_EVENT whenever a UAF record is altered, and LOGINOUT calls the
service whenever a user logs in.
|
